

ÜBER 25.000
6000+
5x
ÜBER 6 MIO. $
Schutz von Benutzern in führenden Unternehmen
Smarter Access Management with AI-Powered Assistance
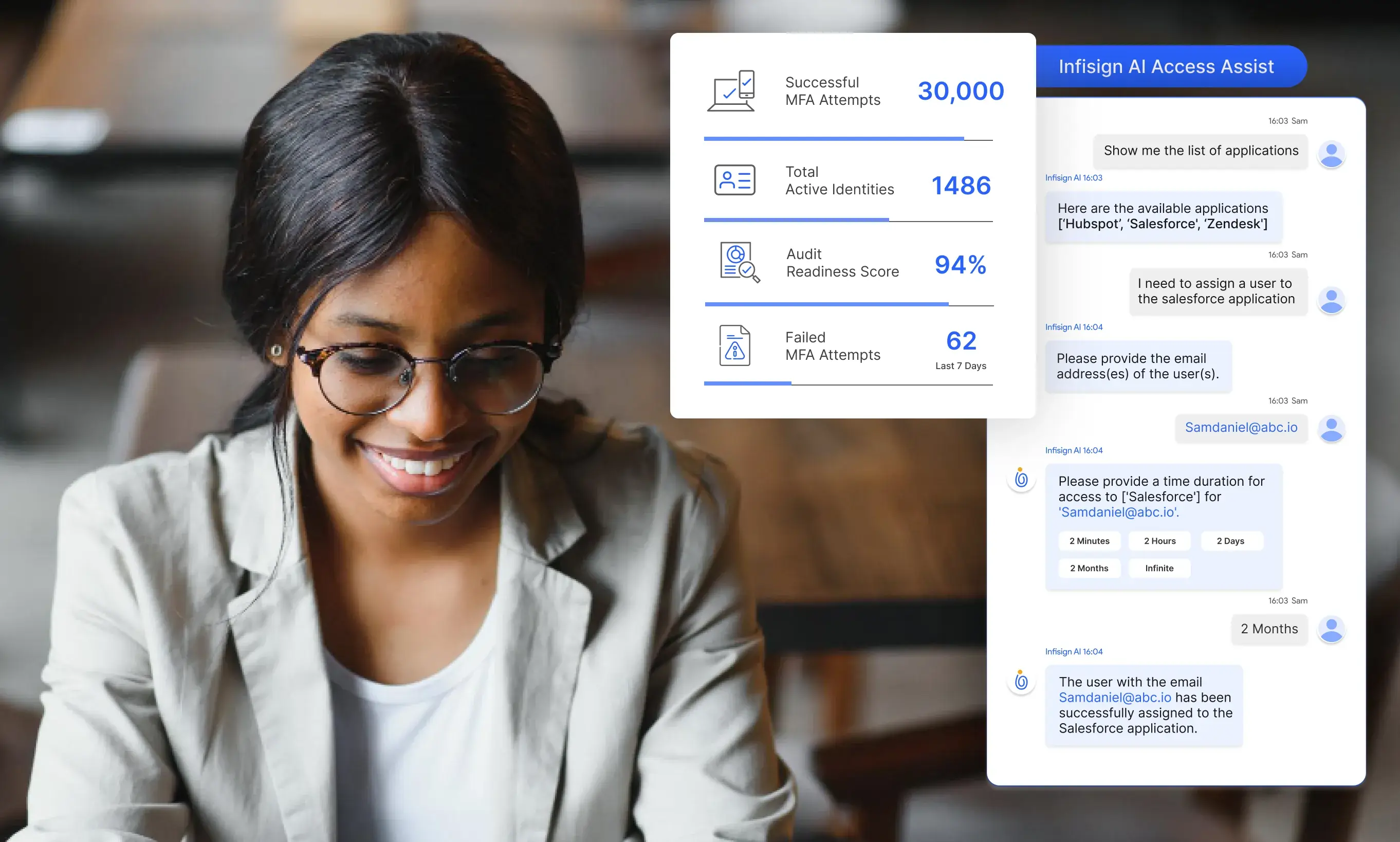
Fast, Secure, and Effortless Access Across Your Tech Stack

Eliminate Phishing Risks
With no passwords to steal, attackers lose their primary weapon. Secure accounts with OTPs, biometrics, or magic links.

No Data Exchanged
With zero-knowledge proof and passwordless authentication, remove the risk of compromised user accounts and credentials.

Better Security and Compliance System-Wide
Weak or overused and overshared passwords are unavoidable. Remove this risk completely for better security system-wide

Stop Data Breaches With Passwordless Authentication
Secure logins with OTPs, biometrics, and QR codes. No passwords means no phishing or credential attacks.

Improve Your UX and Productivity
Approve or revoke user access in seconds using AI-powered access, and access all apps in seconds with passwordless SSO.

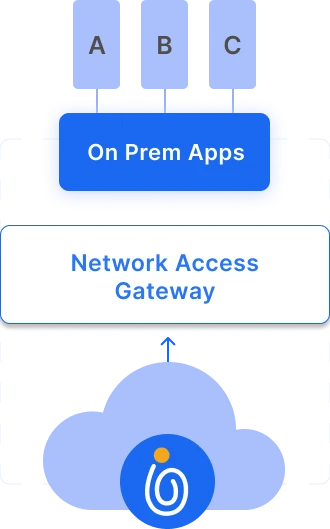
Passwordless Access to Legacy Apps With MPWA
Enable password-free authentication even for applications that don’t support modern identity standards.

Slash IT Support Costs
Remove IT overheads with password resets and access that can be granted for hundreds of users in seconds with ABAC.

Stop Data Breaches With Passwordless Authentication
Secure logins with OTPs, biometrics, and QR codes. No passwords means no phishing or credential attacks.
Go Beyond Legacy IAM With an AI Access Management Solution.

Intelligent Passwordless Authentication


Conversational + Intelligent AI Access


AI-Driven Security for
Non-Human + M2M Identities
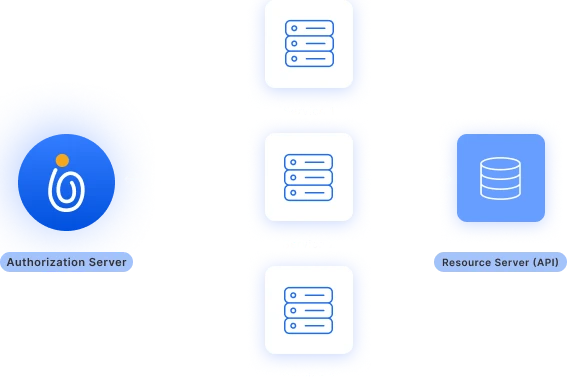

AI-Managed Access for On-Prem Apps to Cloud Servers

Secure AI Decisions with
Advanced Biometrics

Why Choose Infisign On-Premise
Identity and Access Management






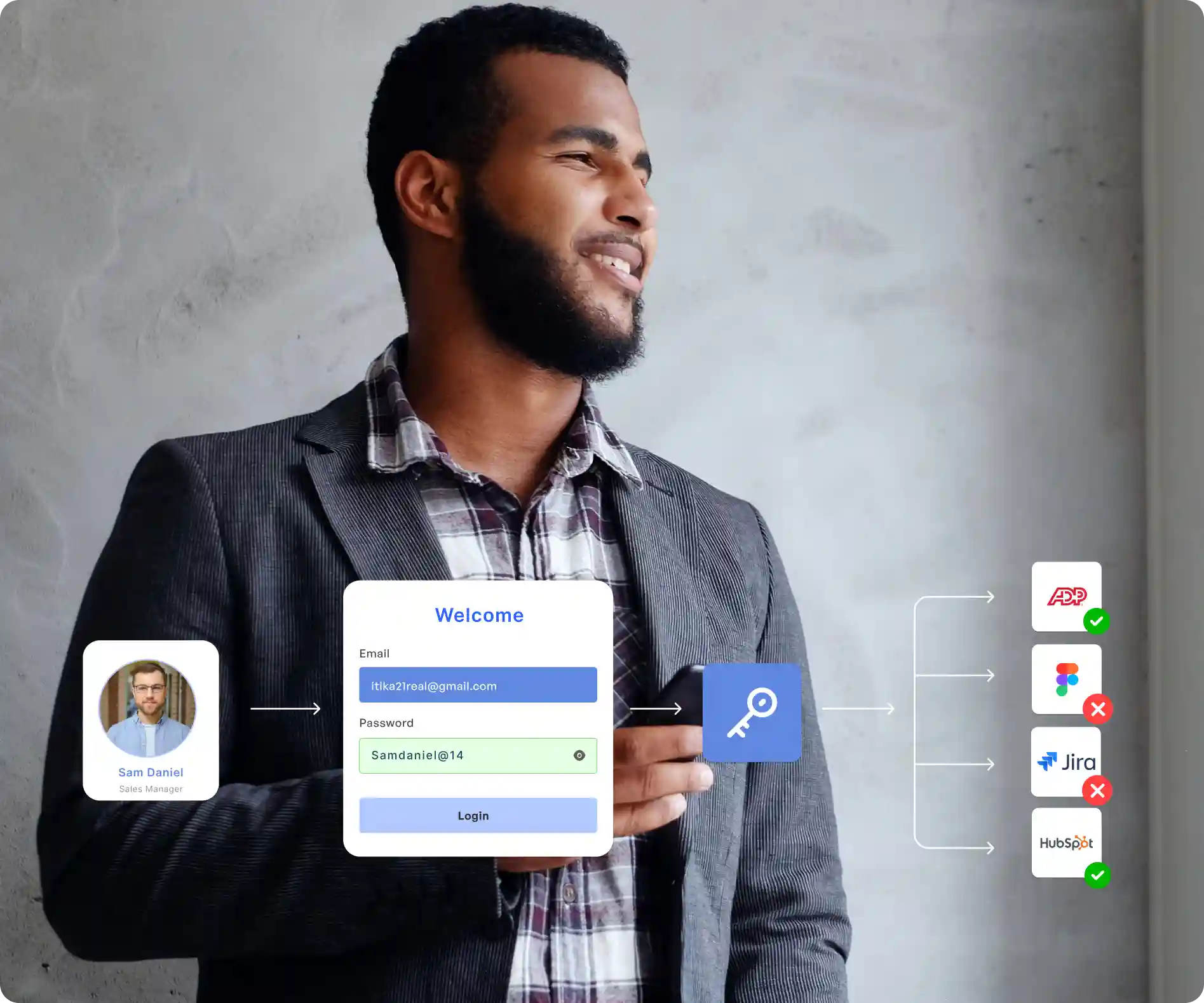
Why Move Towards Passwordless Authentication?
Eliminate Phishing Risks
Adaptive Security With MFA
Better Control With AI-Driven Access
Better Control With AI-Driven Access
Eliminate Phishing Risks
Adaptive Security With MFA
Benefits of Using Infisign’s Adaptive MFA

Remove the Risk of Phishing and Data Breaches
Blocks hackers by removing static credentials. Say goodbye to system breaches from brute force attacks and phishing attempts

Unified Adaptive MFA for Multiple IdP Directories
Simplify security with risk-based MFA policies across ALL directories, from on-prem to cloud, for vendors, distributors, partners, and employees.

Set-Up Takes Less Than 4 Hours
Go from purchase to full deployment in under four hours, securing your entire ecosystem without lengthy project cycles.

Stop Data Breaches With Passwordless Authentication
Secure logins with OTPs, biometrics, and QR codes. No passwords means no phishing or credential attacks.

Stop Password Oversharing
With Infisign, adaptive MFA demands personal verification, stopping the oversharing that invites breaches.

Lower IT Admin Overheads
End unnecessary helpdesk calls and security alerts. Adaptive MFA reduces false positives and actual breaches, easing IT overhead.

Build Trust and Security With Your Brand
Create brand confidence. Adaptive MFA stops password misuse, allowing only verified users to have access to sensitive information.

Stop Data Breaches With Passwordless Authentication
Secure logins with OTPs, biometrics, and QR codes. No passwords means no phishing or credential attacks.
No Passwords, No Breaches Create Secure and Fast Access

Go Passwordless Using SSO and Adaptive MFA
Connect With Over 6000+ Pre-Built Integrations for
an Instantly Passwordless Techstack


.webp)

.webp)
.webp)
.webp)
.webp)
.webp)
.webp)
Different types of authentication








.webp)

Ready to Implement Passwordless Authentication?










FAQs on On-Premise Identity and Access Management























.webp)














