Slow access STOPS productivity - but user provisioning tools solve this.
They also remove the chance of data breaches due to human error, which often leads to EXPENSIVE fines!
For any tech company, uncontrolled access invites disaster. Which is why we're unveiling the top user provisioning software that delivers instant, secure access, enterprise-wide.
What is User Provisioning Software?
User provisioning tools automate the process of granting access to users to the tools or software by automating access once onboarded based on groups, departments, or attributes.
Conversely, these tools also take away entry for users when they depart. This helps lower costs. These costs typically relate to over-granting access or paying for unneeded licenses.
The user provisioning process helps bring these costs under control. Also, as per Gartner, 45% of companies experience interruptions by third-party cybersecurity risks.
User provisioning software paired with advanced authentication removes third-party cybersecurity risks completely.
Top User Provisioning Software Compared
Best 10 User Provisioning Software for Your Company
1. Infisign
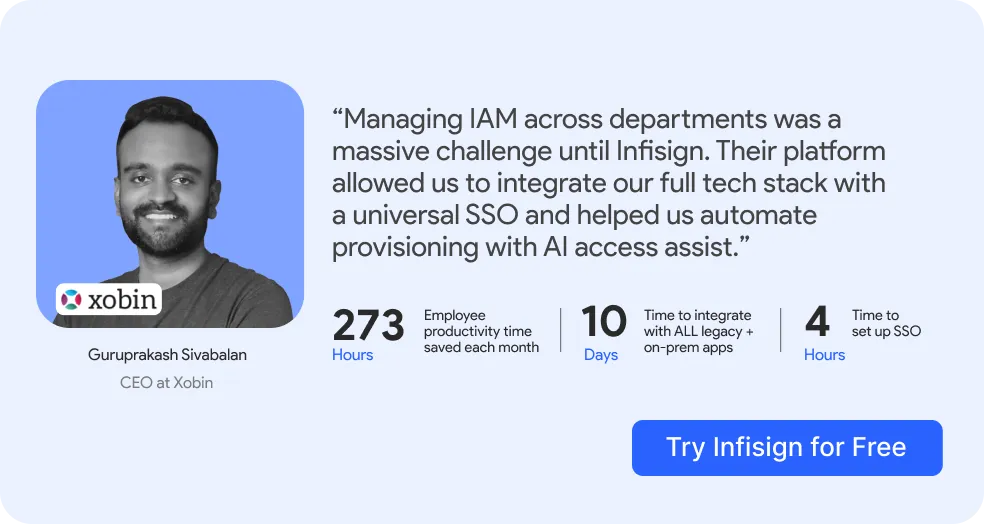
Infisign is an AI-powered user provisioning software, making sure there is continuous verification of users and devices. This ULM tool makes managing account provisioning and deprovisioning a lot quicker with ABAC, RBAC, and AI interfaces.
With AI access assist and adaptive MFA, Infisign makes access both secure and easy. With over 6000+ API + SDK integrations with tools like AWS, GCP, Dayforce, and ADP, there are no security gaps in your tech stack.
For applications, it helps support legacy apps and on-prem apps that do not have SSO or directories to provision users. That said, it also supports multiple identity federation protocols like SAML, OAuth, and OpenID, immediate and secure access. Infisign helps enable unified passwordless authentication across applications.
Infisign also comes with automated workflows and real-time activity tracking. On the whole, it’s one of the top user provisioning software for AI capabilities that eliminate security threats and scale compliance.
Key Features:
- AI Access Assist: AI Access Assist makes access quicker and scalable. It does this by allowing access approvals on Slack, Teams, and AI chat interfaces for entire departments, roles, or individual users.
- 6000+ API Integrations: Stop worrying about protecting your tech stack by using over 6000+ pre-built API + SDK app integrations. Avoid shadow IT with complete integration.
- Universal SSO: Infisign’s SSO allows your teams and users to log in to multiple apps with a single login. Stop password fatigue and oversharing.
- Just In Time Access: With Just in Time access, you can grant third-party users or internal users temporary access for any limited amount of time you want. Remove the risk of overprovisioning.
- Adaptive MFA: This makes sure that your software is accessible through biometrics, OTPs, magiclinks, push notifications, and even authenticator apps. This adds multiple layers of authentication that are quick and easy to do.
- Supports Legacy + Web-Based Applications: Most IAMs ignore the older software with MPWA (Managed password web authentication). Infisign makes sure that you do not have to enable SSO functionality.
- Attribute-Based Access Control: With attribute-based access control (ABAC), you go one level deeper than RBAC. Add and remove hundreds of users in one go based on the attributes you choose.
How Infisign Unified Multiple IdPs for a Global Manufacturing Giant
Infisign acts as a central identity gateway for one of our MAJOR manufacturing clients’ fragmented identity landscape. We removed productivity bottlenecks, security risks, and EXPENSIVE delays.
Infisign unifies the entire ecosystem, bridging disparate directories and tools without replacing costly legacy infrastructure.
How Infisign Helped Our Leading Manufacturing Client:
- Shattered Identity Silos: Created a single source of truth by syncing with all existing IdPs (like Azure AD, Cognito), instantly bridging disparate systems.
- Universal Single Sign-On (SSO) Experience: Delivered a true Single Sign-On experience, authenticating users once for secure, immediate access to every application they need.
- Effortless Legacy App Access: Wrapped decades-old, on-premise applications in a zero-trust security framework, removing vulnerabilities without rewriting a single line of code.

Pros
- AI-powered access makes provisioning users instant
- Has ALL advanced authentication features without additional costs
- Add or remove access for full teams, locations, and departments. This can be done in one go with ABAC and RBAC
- Unlimited directory sync and migrations
- Works across multiple ecosystems and legacy apps that are not compatible with each other
Cons
- Passwordless authentication for SSO can only be enabled through the password vault
2. Okta
Okta is easily one of the top IAM software choices for large businesses. This software assists with access control. It also addresses potential dangers like fake app threats and compliance needs.
Okta also improves user setup with automation. These are automations that support HR systems such as Workday and Active Directory. This provisioning tool also adds MFA and SSO for quickness.
New user profiles start the setup for apps, emails, and devices. This allows for fast logins and user activity.

Key Features of Okta:
- Lifecycle Management that automates onboarding and offboarding.
- Has Granular Deprovisioning for the removal of access for departing users.
- Pre-built support for over 7,000 apps mitigates risks like fake apps and malware.
- Role-Based Access Control that adjusts permissions dynamically as users change roles.
Pros
- Improved control and data protection
Cons
- Limited compatibility and does not work with older or legacy apps
- Not suitable for smaller or medium-sized companies
- It can get expensive for advanced security that most enterprises require
3. OneLogin
OneLogin’s reliable automated user provisioning makes it the top user provisioning software. This goes especially for workforce identity management. This user provisioning tool removes the need for manual user setup. It does this by using its flexible mapping engine.
This engine assigns permissions, roles, and app entry. This is based on pre-set rules allowing for accuracy and speed.
OneLogin’s system also connects smoothly with Active Directory, LDAP, and other identity sources.

Key Features of OneLogin:
- With Dynamic Mapping Rules, it makes complex workflows automatic. This makes automatic app access assignments
- Using Active Directory Sync, it keeps user data consistent across platforms. This happens as and when updates occur
- It comes with an Application Catalog. This permits pre-configured apps easy SSO connection
Pros
- Simplified user login process
- Adds strong account security in multiple checkpoints
Cons
- Some users reported issues keeping multiple devices in sync
- Hard to set up and run without an IT team
- Not ideal for smaller businesses
4. SailPoint
SailPoint’s automated user provisioning permits accurate and efficient entry management. This is throughout the user lifecycle.
With role-based provisioning, it automatically grants or revokes entry to applications and systems. This lessens manual tasks and potential mistakes. This user provisioning software looks after security and compliance. It meets evolving business needs.

Key Features of SailPoint:
- SailPoint dynamically assigns access privileges based on user roles within your company
- Automates user setup for faster and more accurate integration
- Connects with enterprise systems for unified identity management
- SailPoint's adherence to regulations by maintaining secure, auditable access processes with compliance alignment
Pros
- Comes with reliable IGA capabilities for enterprises
- Has strong automation capabilities
Cons
- Has a steep learning curve, which can be complex for some users
- Initial licensing and ongoing maintenance can get expensive
- The user interface could be easier to navigate
5. CyberArk
CyberArk's has an automated setup for privileged accounts. This is across many platforms. It allows secure and efficient entry management.
By using Active Directory and VMware vCenter, CyberArk permits easier onboarding and offboarding. This lessens manual work. It also cuts down potential human mistakes. This user provisioning software contributes to operational efficiency. It also helps you follow compliance needs.

Key Features of CyberArk:
- It has an Accounts Feed. This presents a structured process to find and set up accounts. It matches company standards and policies.
- It uses Auto-Detection Processes. These create local administrator accounts based on predefined templates. This streamlines account management.
- Target Machine Sources supports setup from Active Directory or the platform and VMware vCenter. This allows flexibility and scalability.
Pros
- Has feature-rich tools for PAM
- Good for compliance and auditing capabilities
Cons
- It can get costly and complex to set up
- Features can feel complicated and overwhelm users
6. Jump Cloud
JumpCloud is a reliable user provisioning software for scalability. This allows secure and efficient management of the identities of companies. These are across various IT resources.
This tool can be used on cross-platform environments. JumpCloud supports macOS, Linux, and Windows devices. It also manages entry to cloud-based and on-premise systems.
With Zero Trust principles, JumpCloud uses Conditional Access policies. This improves security. It also simplifies identity governance in dynamic work settings.

Key Features of JumpCloud:
- Centralized user profiles granting controlled access across networks, devices, and applications. Jumpcloud enables this with unified identity management.
- Supports access management across macOS, Windows, and Linux systems.
- Jumpcloud has provisioning for web applications, VPNs, and infrastructure without identity sprawl.
Pros
- Has excellent cross-platform support
- Easy to use and implement
Cons
- Has several OS specific issues and differences
- The documentation can be outdated and have gaps
- End-user self-service is quite limited
7. Microsoft Entra ID
Microsoft Entra ID is a dependable user provisioning solution. It is designed to synchronize and manage user identities. This happens across various cloud and on-premises environments.
With its automation capabilities, it simplifies the identity lifecycle. This ranges from account creation to deprovisioning. It allows secure and smooth entry to business applications.
The platform works with thousands of SaaS applications. It supports hybrid models. It uses tools like Microsoft Entra Connect and provisioning agents. These bridge HR systems, directories, and applications.

Key Features of Microsoft Entra ID:
- It connects with application APIs. This is to make automatic user account creation, updates, and deletion. This is based on defined business rules.
- It supports both cloud-native and on-premises systems. Tools like Microsoft Entra Connect Sync and provisioning agents assist this.
- It allows administrators to set up attribute flows and custom mappings. This is for better user identity synchronization.
- Entra ID makes automatic identity workflows. This is to manage user lifecycle events. These events include onboarding, role changes, and terminations.
Pros
- Has advanced security features that make access control granular
- Powerful when working with the Microsoft ecosystem
Cons
- Limited compatibility with some apps and ecosystems
- Documentation can be outdated
- Costs can get expensive when you have a large number of users
8. Zluri
Zluri is a user access management platform. This user provisioning software is designed to simplify and secure the onboarding and off-boarding lifecycle. This is from onboarding to offboarding. It requires little manual work.
This user provisioning software makes automatic user entry workflows. It also gives better visibility into app usage and entry permissions. Improving these processes gets rid of inefficiencies. It also removes security dangers.

Key Features of Zluri:
- Zluri has Zero-Touch Provisioning. This means fully automated onboarding workflows that ensure accurate and timely access assignment in user provisioning.
- This user provisioning Syncs with HR systems automatically. It uses HRMS Integrations to update user profiles and permissions.
- Securely and automatically revoke access during offboarding to prevent unauthorized use.
- Zluri has centralized dashboards to monitor access, detect anomalies, and manage SaaS licenses effectively.
Pros
- Reliable customer support
- Easy to onboard users
Cons
- Has limited integrations
- Has a few missing authentication and security features
- Hard to navigate some issues due to little documentation
9. Ping Identity
Ping Identity has an identity security platform. This platform makes provisioning automatic. This user provisioning tool strengthens the entire user lifecycle. This is from initial onboarding to eventual deprovisioning. Ping Identity enables this through automation.
This user provisioning solution makes access workflows automatic. It also provides better security. Ping Identity does this by making certain users have fitting access based on centralized policies.

Key Features of Ping Identity:
- It uses standards-based protocols like SCIM. This is to enable automatic user account creation, updates, and deletion with a wide range of applications.
- It supports provisioning to both cloud-based SaaS applications and on-premises systems. This is facilitated by its flexible platform components like PingFederate and PingOne
- Ping Identity automates user lifecycle workflows. This is to manage events such as new hires, role modifications, and employee departures
- It enables administrators to define attribute mappings and transformations. This is for precise synchronization of user identity data between directories and target applications.
Pros
- MFA can function without the internet
- Wide support for API integrations
Cons
- Some users noted notification and sync issues, which delay the workflow
- Support responses can get delayed
- Cost is not suitable if working within a budget
10. Oracle Identity and Access Management
Oracle Identity Manager (OIM) makes automatic and improves user identity provisioning. This user provisioning tool is a dependable solution for managing the lifecycle of user accounts. It also manages entry across business systems.
With its advanced capabilities, OIM handles tasks. These include automated onboarding, role assignments, and entitlements.
Oracle IAM also makes certain secure, auditable workflows. It also connects smoothly with existing IT environments.
Moreover, his provisioning solution supports connectors for SAP, Active Directory, alongside other related tools. On the whole, it can be a key tool for maintaining compliance.

Key Features of Oracle IAM:
- Oracle allows for Advanced Access Controls. This includes role-based access management, segregation of duties, and dynamic policy enforcement.
- Oracle comes with embedded auditing and reporting. This helps create detailed reports on approvals, access requests, and compliance metrics.
- This user provisioning provides tools for managing identity certifications and audits. This helps ensure regulatory compliance.
Pros
- Stable and cost-efficient
Cons
- Misses some essential features
- if you plan to use it without LDAP, you limit your feature set.
How to Choose the Right User Provisioning Software for Your Business?
- Understand Your Company's Needs and Size: First, discover what your business specifically requires from this kind of tool. Think about how many employees you have now. Consider how complex your current computer systems are. For example, are they in your office, cloud-based, or a mix? Also, consider if you plan to grow a lot. This helps you pick a tool that fits now. It should also be able to expand later.
- Check How It Connects with Your Other Systems: The tool must work well with the software and systems you already use. This includes your HR programs. Employee information is stored there. It also includes key IT systems like Active Directory, Azure AD, or Google Workspace for logins and entry.
- Look for Strong Automation and Ways to Customize It: A good tool will automatically handle common tasks. These include setting up new employees. It also includes removing their entry when they leave. And it includes changing what they can do. You should also be able to adjust these automated steps. This is to fit your company’s specific rules and approval processes.
- Prioritize Security and Meeting Regulations: Pick a tool with solid security measures. This means things like controlling entry based on job roles. It also means supporting extra security steps for logging in, like MFA. And it means keeping clear records of who did what. The tool should also help you follow industry rules. Examples are GDPR or HIPAA. It does this by tracking access.
- Make Sure It's Easy for IT and Employees to Use: The user provisioning tool should be simple for your IT administrators to manage well. It is also helpful if it has self-help options for employees. For example, letting them reset their own passwords or request entry. This can make the IT team's workload smaller.
- Consider if It Can Grow with you and Has Good Support: Choose a solution that can handle more users and different needs as your business gets bigger. Also, look into the reputation of the company selling the tool. See how responsive their customer support is. Check if they have good documentation and training. This is for a smooth setup and ongoing use.
Automating Provisioning for All Ecosystems and Tools
User provisioning software is essential for organizations looking to manage user lifecycles and access efficiently while maintaining security and compliance.
Take the time to assess your company's specific needs, such as automation in onboarding and offboarding, to find the best fit.
With Infisign, you allow AI-Access Assist to help you provision users for ALL ecosystems. It also comes with features like SSO, JIT access and over 6000+ API integrations.
Ready to experience Infisign? Start your free trial today.
User Provisioning Software FAQs
What is the difference between authentication and provisioning?
Provisioning is setting up a user's account and access. Authentication, on the other hand, is proving who you are to use that account, like with a password or code.
What are the three types of provisioning?
The three types of user provisioning are: Manual (done by hand), Automated (software does it based on rules), and Self-Service (users request access themselves).
What does provisioning mean in IAM?
In IAM, provisioning is the process of creating, managing, and removing user accounts and their access to IT systems and applications.




























