Your company has hidden APIs you cannot see. These shadow APIs leak customer data daily. Only 15% of companies know which APIs expose secrets. Hackers love this blind spot. API attacks exploded 400% in six months. 84% of companies got breached last year. T-Mobile lost 37 million customers. Dell lost 49 million customers.
Client credentials flow ends this nightmare. No more risky human passwords. Machines talk directly with secret codes. Hackers cannot steal what they cannot see. Setup finishes in one afternoon.
What Is Client Credentials Flow?
Client credentials flow is an OAuth 2.0 method for app authentication. Modern business applications exchange data with external services each day. Apps like CRMs, payment processors, and inventory systems need secure connections. This method, also known as the oauth2 client credentials flow, lets apps prove their identity using secure credentials. No human login intervention is required for these processes.
- Direct Application Communication. Apps communicate server-to-server without web browsers or user interfaces. This direct approach eliminates many common security vulnerabilities. It reduces complexity in your system architecture.
- Credential-Based Authentication. Each app must register with an authorization server first. Apps receive unique credentials during this registration process. Credentials include a client ID and a secret key. The client ID can be public but secrets must stay private.
- Token-Based Access. Apps present credentials to authorization servers when accessing resources. Servers verify credentials and issue access tokens afterward. This process, commonly referred to as the client credentials grant, grants permission to use specific services. Tokens expire to maintain security over time.
- Controlled Permissions. Administrators define what each app can access during registration. Apps get minimum permissions needed for their functions. This reduces security risks if credentials get compromised. Permission controls keep different systems separate from each other.
Key Components of Client Credentials Flow
The OAuth 2.0 client credentials flow requires three essential components. Each component serves a specific purpose in authentication.
This modular architecture enables scalable system design. Each component can scale independently as needed. You can monitor each component for security issues. This approach simplifies security management across enterprise systems.

Here are the three parts that make everything work smoothly.
- Client App is your service that needs data from somewhere else. It keeps its secret safe and asks for tokens when needed.
- Auth Server handles the checking work and makes new tokens. It keeps track of who can do what things.
- Data Server guards your APIs and files using token-based authentication rules. It always checks tokens before sharing anything.
- Secret Codes include your app ID and password that prove who you are. These must stay hidden from bad people.
How the Client Credentials Flow Works: Step-by-Step
The client credentials flow follows four simple steps for authentication. All communication happens through secure server connections between applications.
The client credentials grant flow takes milliseconds to finish without delays. Each step includes security checks to prevent malicious attacks. This blocks unauthorized users from stealing credentials during transmission. All messages travel through encrypted communication channels for protection.
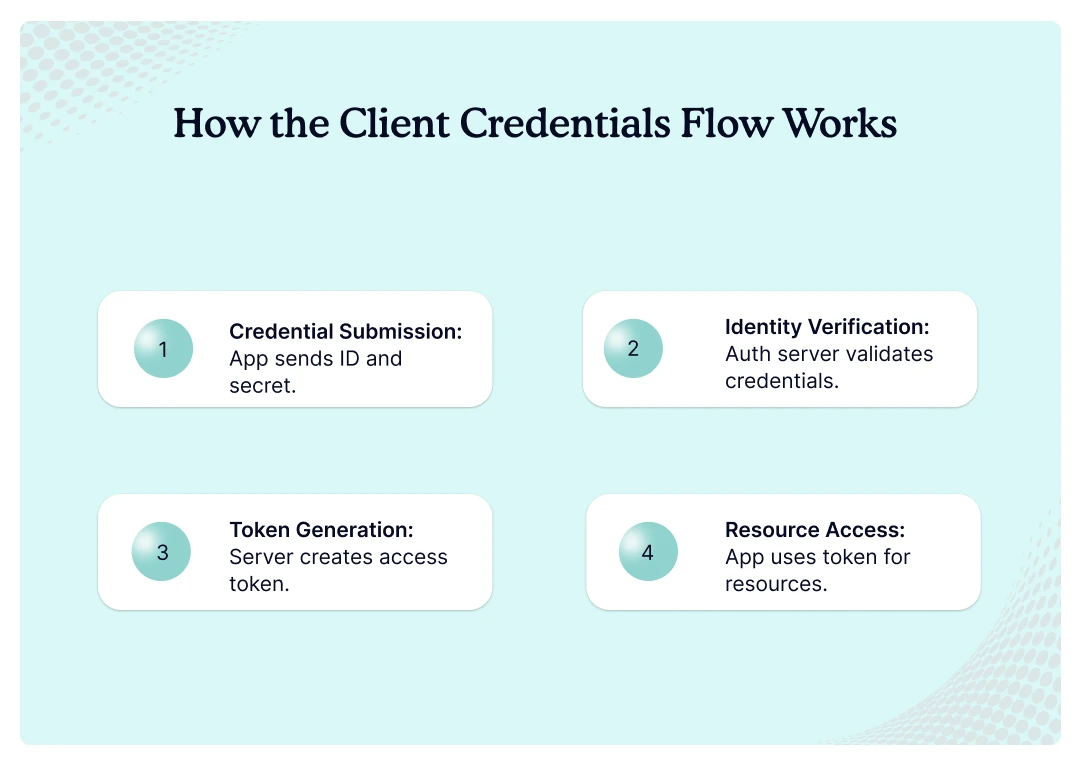
Here are the four sequential steps that complete the authentication process:
- Credential Submission. Your app shares its ID and secret with the auth server. It tells the server what kind of access it wants. The server receives these credentials for verification checks.
- Identity Verification. The auth server looks up your codes in its database. It makes sure you are real and active. The server validates credentials against stored registration information.
- Token Generation. Server creates a new access pass with the right permissions. It includes when the token will stop working. The token contains scope and expiration information for security.
- Resource Access. Your app shows the token to data servers. They check the token and give you requested resources. Servers verify token validity before granting access to data.
What Are the Main Use Cases for the Client Credentials Flow
The OAuth client credentials flow works best for applications that run without people. Your backend services use this method each day for operations. Your business connections with other companies depend on this method. Machine-to-machine authentication keeps these automated processes secure and reliable.

These five scenarios work best with the client credentials flow:
- Microservices Communication. Small services talk to each other inside your app. Each service proves who it is using login codes. Services authenticate before sharing data or processing requests.
- Third-Party API Integration. Your company needs to connect with outside APIs without user login screens. Partner companies need secure access to your business data. These automated connections let companies exchange information safely without manual login steps.
- Scheduled Job Processing. Scheduled jobs need to access databases at set times. These programs cannot wait for people to log in. Jobs run during off-hours when staff is not available.
- Real-Time Data Synchronization. Data sync between systems happens all day without people watching. Real-time feeds need constant access to update information. Systems push and pull data based on business requirements.
- Administrative Automation. Admin tasks require special access to manage accounts behind scenes. These operations happen without human intervention for efficiency. System maintenance and user management tasks run through automation.
Benefits of the Client Credentials Flow
The client credentials flow makes systems faster and safer for automated applications. It cuts out complex user steps that slow down automated work. The flow handles heavy traffic better than old login methods. Security gets better through controlled access with pre-made accounts for applications.
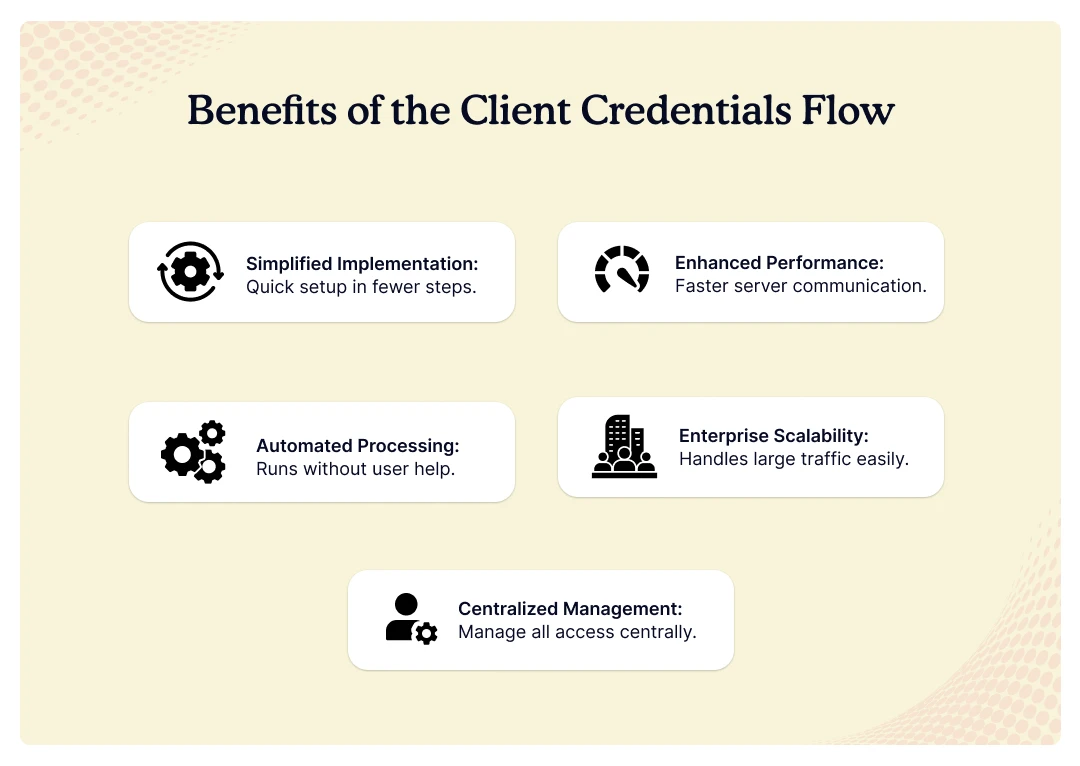
These five key advantages make this flow essential for modern business applications:
- Simplified Implementation. Easy setup needs fewer steps than user login methods. You skip browser redirects and callback handling in code. Your dev teams can add authentication faster with fewer resources needed.
- Enhanced Performance. Fast speed happens because servers talk without browser overhead. You cut waiting time for key business tasks. Direct server talk reduces delays and makes response times better.
- Automated Processing. Processes work without human help or manual work. Your scheduled jobs run without login breaks or delays. Background services work without user help for non-stop operation.
- Enterprise Scalability. Scale becomes possible through special login setup for high volume. This setup handles millions of token requests without speed issues. Load sharing spreads login requests across multiple servers.
- Centralized Management. Control lets admins manage all app access from one place. Access removal takes effect across all systems without delays. Permission changes spread to all connected services and apps.
Security Best Practices for Implementing Client Credentials Flow
Setting up the client credentials flow refresh token needs careful attention to security details. Your secret codes must stay safe and hidden from log files. Token checking must happen on every data request. This stops bad people from using stolen or fake tokens.
Current security rules say you need extra protection layers beyond basic checking. This includes network limits and token rotation plans. Complete tracking logs help you spot problems fast. Good setup prevents common attacks like code theft and token replay.
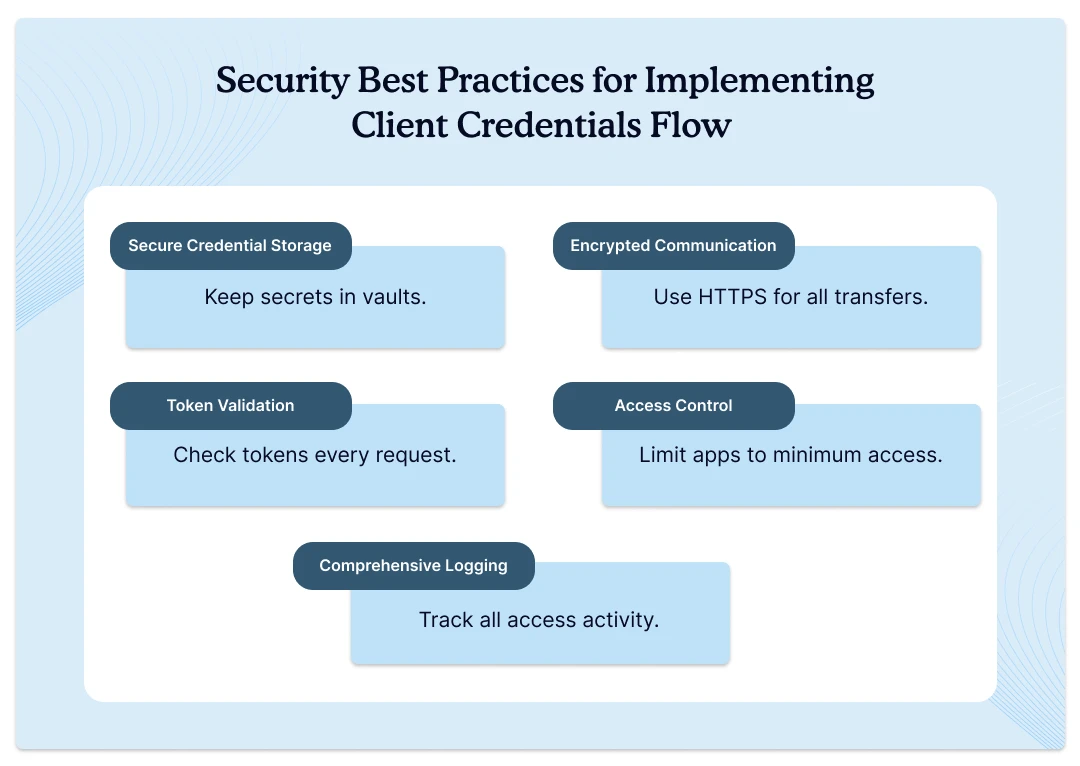
Follow these key security rules to protect your setup.
- Secure Credential Storage. You must store secrets in encrypted vaults instead of plain text files. Never put secrets in source code that others might see. Use environment variables or secure key management systems.
- Encrypted Communication. You must use HTTPS for all communication between system parts. This prevents hackers from stealing codes during data transfer. All API calls need SSL/TLS protection.
- Token Validation. You must check tokens on every data request for proper permissions. Your data servers need to verify tokens with auth servers often. Invalid tokens should be rejected immediately.
- Access Control. You must limit app access to only what they need. This reduces damage when hackers steal your credential codes. Follow the principle of least privilege.
- Comprehensive Logging. You must log every login attempt and data access activity. This helps your security team spot problems and respond to attacks. Monitor for unusual access patterns.
Challenges in Client Credential Flow
Client credentials flow brings setup challenges you will face. Secret management gets harder with more apps. Different environments need separate credentials. You need systems for token rotation and monitoring.

Here are the main problems you will face during setup.
- Environment Security. You need secure processes to share codes between development and production environments. Each environment must have its own separate credentials.
- Secret Updates. You must update secrets across all your apps and servers together. This change cannot break your running services.
- Performance Monitoring. You need to watch system speed as more logins happen. Token checking will slow down without good performance tuning.
- Error Management. Error handling becomes hard when many services use one auth server. Network issues will affect your entire system at once.
- Compliance Requirements. Your compliance rules may require special security controls and detailed reports. These requirements make your basic setup much more complex.
Making the Right Call for M2M Auth
OAuth 2.0 client credentials flow works best for automated systems. Check your security needs and speed requirements first. This flow works great for backend services and microservices. It does not work well for user login scenarios.
Consider other authentication methods if users need to log in. Use different flows when you need complex permission settings. Client credentials give you strong security and fast performance. Choose this flow when you want simple automation.
These factors help you choose the right login method:
- No User Interaction. Client credentials flow fits automated processes perfect. User flows create unnecessary complexity for machines.
- High Speed Requirements. Client credentials favor speed over other authentication methods. Direct server communication provides the fastest authentication.
- Simple Permission Model. This works when applications need consistent resource access. Complex permission scenarios require different authentication flows.
- Long-Running Services. Services benefit from automatic token refresh without users. This approach ensures continuous system operation.
- Internal System Integration. This works well when you control both components. External integrations require additional security measures.
Infisign builds OAuth 2.0 solutions for your business. The platform makes client credentials setup easy. Your security standards stay strong. Modern companies need reliable machine authentication that grows with them.
- Complete OAuth Support. Protocol support includes client credentials flow. Enterprise security controls come built into the platform.
- Advanced Auth Server. The server handles credential validation and token creation. High-performance architecture scales with your business growth.
- Automated Credential Rotation. This eliminates manual secret management complete. Continuous service operation runs without any interruptions.
- Complete Audit Logging. The system tracks all login attempts. Access patterns provide compliance reporting for your organization.
- Pre-Built API Integrations. The platform works with thousands of apps. Rapid deployment works across existing enterprise infrastructure.
- Network Access Controls. The system restricts usage to authorized networks. This prevents credential abuse from compromised systems.
- Real-Time Monitoring Dashboards. Dashboards show login patterns clear. Security events display across your entire OAuth setup.
- Professional Support Services. Services guide setup best practices. Ongoing security consultation handles complex enterprise requirements.
Ready to implement secure client credentials flow for your company?
Book a free demo to see how Infisign simplifies enterprise machine-to-machine authentication.
FAQs
What is the difference between client credentials flow and user flow?
Client credentials flow lets apps log in by themselves without needing people. The app uses secret codes to get a token automatically. In user flows, a person must log in and give permission on a screen. That means user flows are for checking who the person is, while client credentials flow is for checking which app is asking. This makes client credentials flow faster and better for backend services that run on their own without anyone watching.
What is the difference between OAuth2 and client credentials?
OAuth2 is a full system that helps apps get permission to access things. It has different ways to do this, called flows. One of these flows is called client credentials. This flow is made for when two apps talk to each other, not for when people log in. OAuth2 can be used when users need to log in, but client credentials are just for app-to-app communication. OAuth2 gives the rules, and client credentials is one way to follow those rules for letting apps prove who they are.




























