Your AI agent just accessed your bank account. It modified your database and sent emails to clients.
This is exactly what's happening with MCP authentication systems today. Security breaches occur daily across organizations. Hackers exploit weak authentication systems constantly.
One compromised token gives attackers complete access.
Understanding MCP security isn't just nice-to-have anymore. It's critical for anyone building AI systems in 2026. Here's why it matters so much.
What is MCP and Why It Matters in Modern Authorization
MCP stands for Model Context Protocol. It's the universal translator for AI systems. You can think of it as a bridge between worlds.
Your AI can talk directly to Gmail servers. It accesses databases instantly. It controls Slack channels automatically. It connects to hundreds of business tools seamlessly.
MCP eliminates the barriers between AI and applications. Before MCP, AI lived in isolation. It couldn't touch external services. It couldn't modify real data. MCP changes everything by creating secure communication channels.
But here's where it gets interesting. Without proper security, this connection becomes your biggest vulnerability.
Understanding MCP's role in modern authorization isn't just technical knowledge. It's business survival. Here's why this matters for your organization:
- The Connection Challenge. AI systems used to be isolated islands completely. They couldn't touch external services at all. MCP breaks down these barriers completely. It enables AI access while creating attack surfaces.
- The core MCP components include servers that expose capabilities, clients that consume services, and transport layers that handle communication. Resources define what data AI can access. Tools specify what actions AI can perform. Prompts guide AI behavior within defined boundaries.
- Risk Amplification. When AI can suddenly access everything, security flaws become catastrophic. One compromised token could give attackers access. They get access to your entire digital ecosystem.
- Enterprise Reality Check. Companies like Block and Apollo are running operations through MCP. This makes enterprise-grade security a basic requirement now.
- The Standardization Win. Custom integrations are security nightmares where connections become vulnerabilities. MCP standardizes everything completely. It makes security patterns repeatable across systems.
- Explosive Growth. The ecosystem grew from zero to 1,000+ servers quickly. This creates more opportunities for innovation completely. But it also creates more potential security disasters.
Now that you understand why MCP matters completely. Let's dive into what MCP authentication actually is.
What is MCP Authentication?
MCP authentication is the security system that verifies who can access your AI tools.
MCP authentication uses OAuth 2.1 standards to protect your data. It checks identity before allowing AI agents to access external systems. The system validates credentials continuously. It monitors every request for suspicious activity.
Here's how MCP authentication protects you:
- Identity Check First. Every request gets challenged before processing. The system asks for proof of identity. It verifies credentials before allowing data access.
- Permission Verification. Getting authenticated is just step one. The system then checks what you can do. It verifies your permissions across all resources.
- Smart Token Management. Modern MCP systems use short-lived access tokens. They rotate automatically for extra security. These work like temporary digital passes.
- Multi-Layer Protection. Security operates at different levels. Network encryption protects data movement. Application validation checks every request. User permissions control resource access.
- Context-Based Control. Your access changes based on location and time. Office network access differs from remote connections. Unknown locations trigger additional security checks.
- Complete Activity Logs. Every login attempt gets recorded with timestamps. Permission checks get saved for compliance. This creates comprehensive audit trails.
Authentication handles the "who" question completely. Understanding the "how" is equally important for success.
How MCP Authentication Works
MCP authentication runs on OAuth 2.1 standards. It's like a security checkpoint that checks every AI request.
The system uses multiple security layers. PKCE prevents code theft. Dynamic Client Registration enables auto setup. These components create strong security.
Here's how the technical flow works:
- Discovery Step. Your AI hits the MCP server first. Server sends back 401 error with special headers. Headers point to security endpoints. AI fetches server details automatically.
- Auto Registration. AI registers itself with the server. It sends names and redirect links. Server gives back a client ID. No manual setup needed.
- Security Code Creation. AI creates a random secret code. It makes a challenge from this code. The challenge goes to the server during login. Only original code can finish the process.
- User Login Flow. The user gets sent to the login page. They enter their password and see the permission screen. After approval, the server gives temporary code. This code typically expires within 10 minutes.Code expires in 10 minutes.
- Token Exchange. AI swaps temp code for real access token. It proves ownership with original secret code. Server checks everything matches. JWT token gets created with permissions.
- API Calls. Every request includes the Bearer token. Server checks token signature and expiration. Valid tokens get access to tools. Invalid tokens get rejected.
This process ensures security without making AI wait. But authentication is just the beginning completely. Authorization determines what happens after you're verified.
MCP Authorization Models
Authentication gets you in the door. MCP authorization decides what you can do inside. This is where smart permission control becomes critical.
MCP supports different authentication models and authorization patterns. Each model serves specific use cases. Your choice depends on security needs and infrastructure.
Authentication Models:
- OAuth 2.1 Flow. The main standard for MCP authentication. Uses authorization codes for user login. Includes PKCE for extra security. Works with external identity providers.
- API Key Authentication. Simple method using static keys. Good for machine-to-machine communication. Keys stored in environment variables. Not recommended for production systems.
- JWT Token Authentication. Self-contained tokens with user information. Includes signature validation and expiration times. Works well for stateless systems. Supports role-based access control.
- Device Flow. Special OAuth flow for local applications. User logs in on different device. Good for CLI tools and desktop apps. No browser required on the target device.
Authorization Models:
- Role-Based Access Control. Users get assigned specific roles like admin or viewer. Each role has different permissions. Admin can delete files, viewers can only read. Clear permission boundaries.
- Scope-Based Permissions. OAuth scopes define what actions are allowed. Example scopes include read-only or write-access. Tokens carry specific scope information. Fine-grained control over API access.
- Resource-Level Security. Each resource has its own access rules. Gmail access doesn't give database permissions. Systems stay isolated from each other. Prevents privilege escalation attacks.
- Context-Aware Authorization. Permissions change based on location and time. Office access differs from home access. Suspicious behavior triggers extra checks. Dynamic security adjustments.
MCP Server Authorization Design Patterns
When building mcp server authorization, you have two main choices. Build your own security system. Or use professional security services. Both work well for different situations.
Here are both approaches:
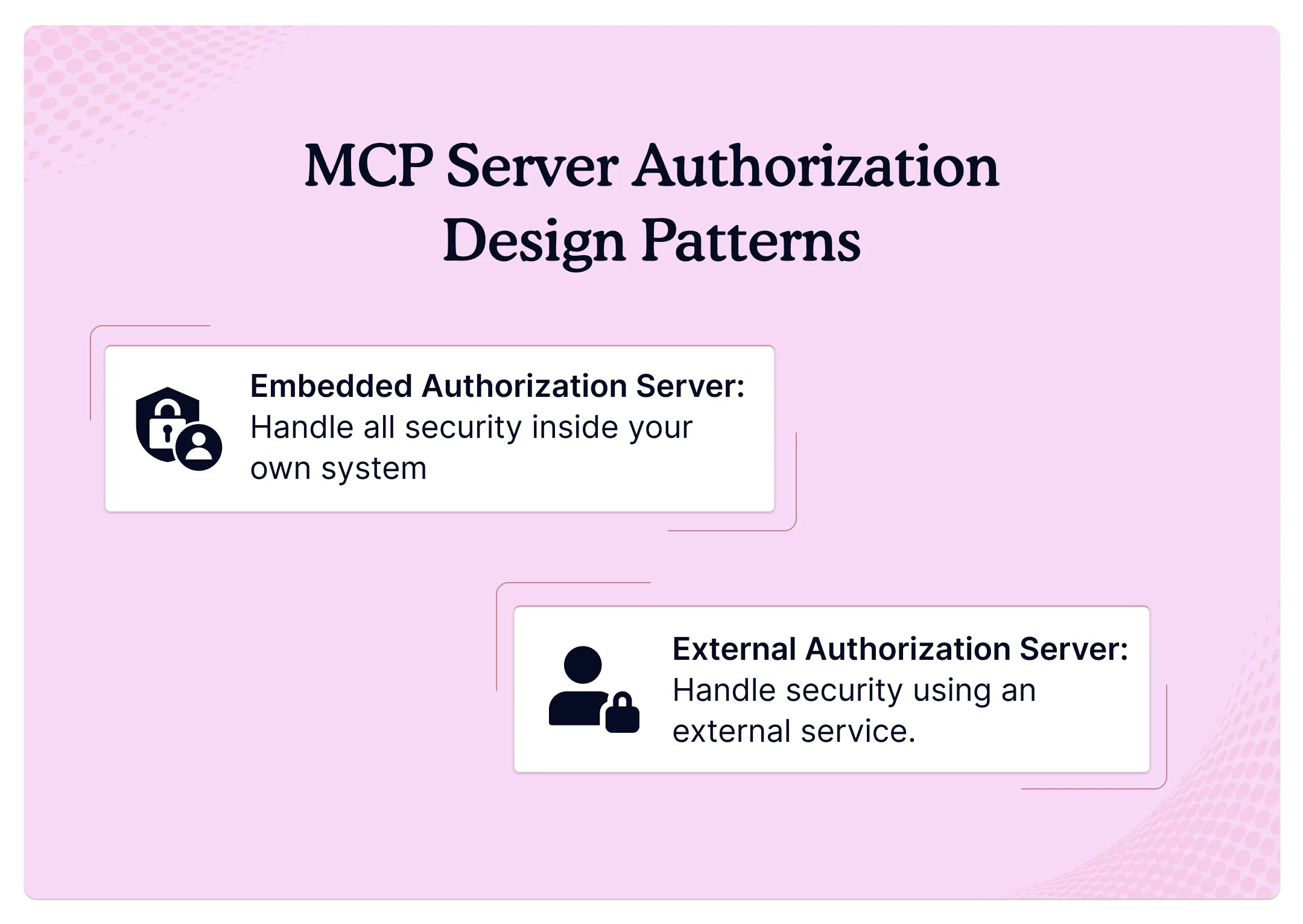
Embedded Authorization Server
You handle all security inside your own system. Complete control over every security decision. But needs serious technical expertise and resources.
What Embedded Server Handles:
- Login screens and user interfaces
- Token creation and validation
- User database management
- Session tracking and timeouts
- Password reset functionality
- Security updates and patches
Here's what you get:
- Total Control. Everything happens inside your system. Login pages, permission checks, token management. You customize every security detail.
- No Dependencies. No external services needed. Everything runs in one place. Simpler deployment for small projects.
- Custom Features. Want special authentication rules? Build them yourself. No limits from external providers. Perfect for unique business needs.
- Heavy Work Required. You implement OAuth 2.1 standards. You handle PKCE security. You manage token storage. One mistake breaks everything.
- Scaling Problems. Growth makes this complex fast. You need backup systems. Disaster recovery becomes critical.
External Authorization Server
Professional security services handle the complex parts. You focus on your core business. Experts manage authentication infrastructure.
What External Server Handles:
- OAuth authorization flows
- User login and registration
- Token generation and validation
- Security updates and patches
- Compliance certifications
- Scaling infrastructure
Here's why this makes sense:
- Less Complexity. External providers handle OAuth flows. They manage security patches. You build business features instead.
- Easy Integration. Already using Google Workspace or Active Directory? Perfect integration with current systems. Users keep familiar passwords. Single sign-on works everywhere.
- Proven Security. These providers handle millions of users daily. They've seen every attack type. Your custom solution hasn't faced real threats.
- Auto Scaling. Need 10 users or 10 million? External providers handle growth automatically. No emergency server calls at night.
- Built-in Compliance. SOC 2, GDPR, HIPAA certifications included. That saves months of paperwork and audits.
Which Option Should You Choose?
Choose Embedded Authorization When:
- You need complete control over security logic
- Your team has deep OAuth expertise
- You want custom authentication workflows
- Data sovereignty requires internal control
- You have budget for security infrastructure
- Compliance allows self-managed systems
Choose External Authorization When:
- You want proven security without complexity
- Your team focuses on core business features
- You need rapid deployment capabilities
- Budget constraints limit security investment
- Compliance requires certified systems
- You already use identity providers like Auth0
The choice depends on your team size, security expertise, and business requirements. Most organizations benefit from external authorization services.
Security Considerations in MCP Authentication
MCP security faces serious problems today. Most MCP servers use weak login systems. Code injection attacks break into 43% of servers. Token stealing happens daily across organizations. Business teams see 327% more cyber attacks.
Companies like Infisign recognize that proper login systems become the foundation for secure AI operations. Without strong security measures, your MCP setup becomes a business risk.
These security problems need quick action from development teams. Here are the critical security issues you must fix:
- Basic Security Problems. MCP focused on features over security first. Basic safety rules got skipped during building. OAuth flows remain incomplete. This creates big gaps in authentication systems.
- Code Attack Problems. Nearly half of MCP servers have injection vulnerabilities. SQL injection and command execution flaws exist. Files leak out through path traversal attacks. These weak spots expose entire systems to hackers.
- Token Stealing Problems. Stolen OAuth tokens give full user access rights. JWT tokens lack proper validation checks. Bad token storage makes stealing easy for attackers. Organizations need strong token management like Infisign provides.
- Server Trust Problems. Installing unknown MCP servers creates serious risks. Certificate validation gets skipped often. Fake servers copy real services perfectly. Always verify server signatures before using them.
- Business Rule Gaps. Many setups lack proper audit logging systems. RBAC permissions stay poorly configured. Data controls remain weak across deployments.
The Next Phase of MCP Implementation
The MCP ecosystem is growing fast. It has significant implications for enterprise security. The technology went from concept to 1,000+ servers. This represents tremendous opportunity and serious challenges.
Here's what's happening in the ecosystem now:
- Standards Are Maturing. The June 2026 update brought comprehensive overhauls. OAuth Resource Server classification became mandatory. This ended the era of delayed security.
- Enterprise Adoption Wave. Companies like Block, Apollo, and Sourcegraph use MCP. They use it for real business operations. This signals the technology's readiness for production.
- Security Evolution. MCP is experiencing rapid security maturation. Similar to early web applications. Better tools, clearer guidelines, and fewer incidents emerge.
- Registry Solution. The planned official MCP registry includes security validation. It will function as a curated marketplace. This helps separate legitimate tools from malicious ones.
- Compliance Frameworks. Organizations are building adaptable compliance systems. They prepare for changing regulations. Companies preparing comprehensive frameworks maintain competitive advantages.
This evolution shows results in real-world implementations. It spans different industries and use cases.
Real-World MCP Authentication Use Cases
Current MCP authentication deployments show significant business value. They span diverse industries. These implementations prove that proper security enables capabilities. It maintains operational safety.
Here are examples of what's working now:
- Developer Productivity Revolution. Developers execute SQL queries directly from editors. They don't switch applications. Authentication systems ensure production data remains protected. This enables seamless workflows.
- Sales Team Transformation. Sales representatives using AI-powered CRM integration achieve results. They achieve 15-25% higher conversion rates. AI generates personalized proposals while authentication keeps information secure.
- Creative Industry Disruption. Digital artists create complex 3D models in Blender. They modify designs in Figma through AI. Authentication protects valuable creative assets from unauthorized modifications.
- Customer Service Revolution. AI agents handle thousands of WhatsApp conversations daily. They also handle phone calls. They access customer history instantly while maintaining privacy.
- Multi-Agent Orchestration. Specialized AI agents coordinate like digital workforces. This includes research, planning, and execution agents. Authentication ensures each agent maintains proper boundaries.
These success stories demonstrate what's possible. Security must be implemented correctly. But building secure MCP authentication remains challenging.
Secure MCP Authentication Powered by Infisign
Building secure MCP authentication from scratch is hard. It's really hard. That's why we built Infisign. It handles all the complex stuff. You don't need to become a security expert overnight.
Here's what makes Infisign different for MCP authentication:
- Complete OAuth 2.1 Implementation. We handle every OAuth flow you can imagine. PKCE, Dynamic Client Registration, Authorization Server Metadata. All the acronyms your security team loves. You just plug in and go.
- Zero-Trust Everything. We trust nothing by default. Every request gets verified. Every token gets checked. Every action gets logged. It's like having security that never sleeps.
- Smart Token Management. Our tokens rotate automatically. They validate scopes constantly. They revoke instantly when needed. You'll never lose sleep over token security. We've got your back.
- Compliance Without Tears. SOC 2, ISO 27001, GDPR compliance handled. We've got the certifications your compliance team demands. No more spreadsheets tracking security requirements.
- Flexible Architecture. Want embedded auth? We've got you. Prefer external authorization? That works too. Our APIs adapt to your architecture.
Ready to secure your MCP authentication implementation? Get started with Infisign today and see how enterprise-grade security can be effortless.
FAQs
What are the Benefits of MCP Authentication?
MCP authentication provides essential security infrastructure for AI-enabled business operations. It protects sensitive data from unauthorized access and enables secure multi-system integration.
Authentication prevents security breaches, ensures compliance assurance, and maintains business continuity. Without proper authentication, organizations face catastrophic security breaches, compliance violations, and operational failures.
What are the Key Components of MCP Authentication?
The key components are OAuth 2.1 flows. They enable secure token exchange. You also need Authorization Server Metadata. This enables automatic setup. Dynamic Client Registration makes onboarding easy.
You also need Resource Indicators. They prevent token misuse. Session management helps maintain security state. Granular scopes provide fine-grained access control. They work across different resources.
These components work together. They create a comprehensive security framework. They enable AI systems to access external resources. They do this safely while maintaining boundaries. They maintain compliance requirements.




























