What is IBM Security Verify?
IBM Security Verify is the one of well-known Identity and Access Management (IAM) solutions. It is made by the company IBM.
It is built to handle the many security needs of today's companies. It gives them one place to manage and protect user accounts and what they can access online.
The tools work for both employee accounts and customer accounts. It is a key part of making sure access to apps and data is safe and easy.
IBM Security Verify Pricing
The price for IBM Security Verify is based on how much you use it. This is measured in something called "Resource Units" (RUs). This model lets companies pay only for what they use.
- Resource Unit (RU) Model: RUs measure how much your company uses the different tools. You usually buy a certain number of RUs for the whole year.
- Free Trial and Price Estimator: It can be hard to find a simple free trial. You usually need to talk to the IBM sales team to get information about pricing.
- What Affects the Price: The total cost depends on many things. This includes the number of users, what they do, and which features they use.
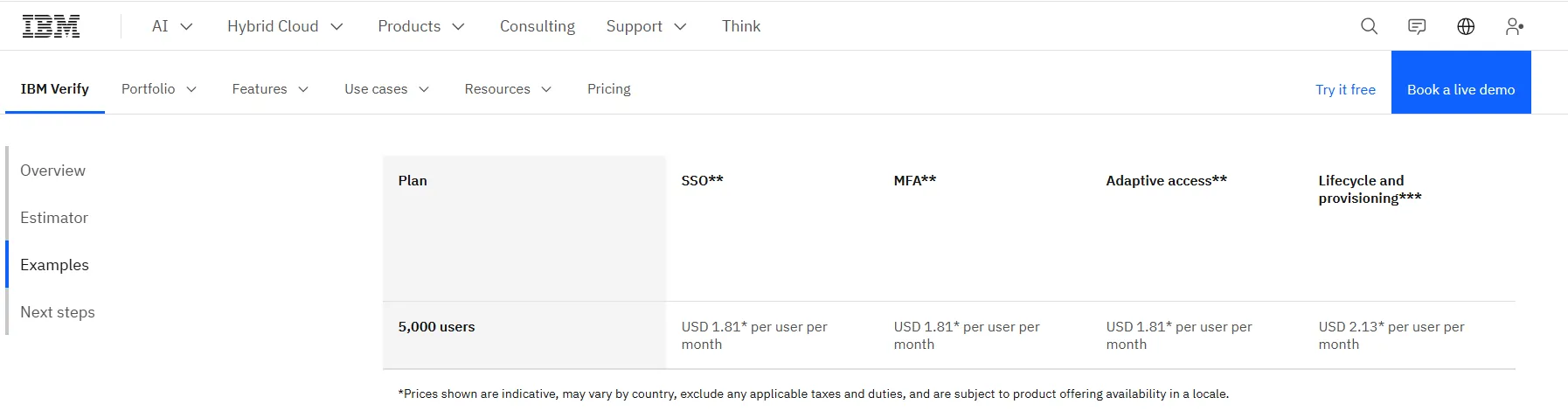
Example Prices: Here are some sample costs per user each month. These are based on a company with 5,000 users.
- Single Sign-On (SSO): $1.71 to $1.81
- Multi-Factor Authentication (MFA): $1.71 to $1.81
- Adaptive Access: $1.71 to $1.81
- Lifecycle & Provisioning/Management: $2.01 to $2.13
As another example, one package for 1,000 users was listed on Amazon Web Services (AWS) for $59,520.00 a year.
These prices are just examples. Your final price can be different.
- There may be extra costs for using systems like AWS. Sales are often final.
- You can ask for a custom price. But because the price is flexible, it can be hard to guess your budget correctly.
- The total cost is not just the price of the software. It also includes the cost of setup time and hiring skilled people to manage it.

IBM Security Verify Key Features
IBM Security Verify has a full set of features built to handle different identity and access management needs in a business. The product list is designed in modules. This lets companies choose the specific features they need.
1. Unified Identity Management (Workforce and Customer IAM - CIAM)
A key strategic quality is its ability to manage both internal (employee) and external (customer, partner) identities with one approach.
- Workforce Identity Management: This makes access simpler for employees and contractors in complex hybrid systems. It helps create a secure and easy work experience.
- Customer Identity and Access Management (CIAM): This part is about creating engaging, modern, and secure digital experiences for customers and partners. It includes features for easy onboarding, self-service, and privacy controls.
- This dual approach allows for consistent tools and policies across different groups of users.
2. Advanced Authentication Mechanisms
Verify provides a rich set of authentication methods.
- Single Sign-On (SSO): This centralizes access control to cloud and on-site applications. It uses open standards like OIDC and SAML 2.0 and has hundreds of pre-built connectors.
- Multi-Factor Authentication (MFA): This is a full suite that includes One-Time Passcodes (OTP by SMS, email, voice, TOTP apps) and push notifications through the IBM Security Verify mobile app. It also includes biometrics (fingerprint, facial recognition), FIDO2/WebAuthn for phishing-resistant authentication, and QR code sign-in. MFA is supported on many devices and systems, including web apps, Linux/AIX, mainframes, Windows Remote Desktops, and RADIUS-protected resources.
- Passwordless Authentication: This promotes methods like FIDO2/WebAuthn, QR code logins, and biometric approvals through the mobile app to improve security and the user's experience.
- Adaptive and Risk-Based Authentication (AI-Powered): This dynamically changes authentication needs based on a real-time risk check. It uses AI/ML and the IBM Trusteer risk engine. The system analyzes device information, location, behavior, and unusual activities to create a risk score. This allows for policies that result in smooth access, requests for more authentication, or blocking access.
3. Identity Governance and Lifecycle Management (Verify Governance)
This module gives wide-ranging abilities for managing the whole identity lifecycle and making sure governance policies are followed.
- Centralized User Management: Gives a single interface for managing user identities and their details.
- Automated User Lifecycle Processes: Supports automatic onboarding, job changes, and timely offboarding, often using SCIM 2.0 for provisioning.
- Control Access Requests: Manage how users ask for and get approval for access to new apps or data.
- Analytics and Reports: Get reports on what users are accessing. The AI can help spot strange activity that might be a security risk.
4. Privileged Access Management (PAM) (Verify Privilege)
This module, which includes technology formerly from Thycotic, works to lessen high-impact security risks from privileged accounts.
Its abilities include secure password vaulting, finding and managing privileged accounts, managing endpoint privileges, recording and watching sessions, and managing secrets for DevOps settings.
5. Access Control and Authorization (Verify Access)
As the next step from ISAM, Verify Access gives complete access management for web, mobile, IoT, and API resources. It supports hybrid setups. It features risk-based access control, identity federation, and mobile MFA.
Administrators can set up detailed access policies based on context like network source, location, device condition, and user or group memberships. It includes the IBM Application Gateway to bring modern authentication to older applications.
6. Consent Management and Privacy
Verify includes features to get, record, and manage user consent for collecting and using personal data. This helps businesses follow rules like GDPR.
This includes automatic data privacy consent workflows and progressive profiling.
7. Integration, Deployment Flexibility, and Standards Compliance
- Supports different deployment types (SaaS, on-premises, hybrid). It follows key industry standards like OpenID Connect, SAML 2.0, SCIM 2.0, and FIDO2.
- It is designed to help meet compliance rules like SOC 2, ISO 27001, PCI DSS, HIPAA, and FedRAMP. It has broad connection options with identity sources and target applications, and solid REST APIs for customization.

IBM Security Verify Usability and Interface
Users have mixed feelings about how easy the tool is to use. It has powerful features, but it can also have problems.
For Admins (IT Teams)
- Hard to Set Up: Admins often say the first-time setup is difficult and takes a long time.
- Clunky Admin Screen: Some say the screen for admins is confusing or looks old.
- Long Time to Learn: The help guides are detailed, but users say it still takes a long time to learn everything.
For Regular Users
- Logging In: Users generally feel that logging in with MFA and SSO works well.
- Helping Themselves: The tool lets users do things themselves, like reset their own password.
- Mobile App Issues: The mobile app has many features. But users have complained that it can be slow or have errors.
IBM Security Verify Reviews and Ratings
IBM Security Verify's position in the market is shown in collected user reviews and industry analyst reports.
- G2: IBM Verify (for general and CIAM services) usually gets an overall rating of about 4.3 out of 5 stars, from over 100 reviews.
- Gartner Peer Insights: For User Authentication, IBM Verify has a rating of 4.5 out of 5 stars from 13 ratings. In the wider Access Management market, Gartner Peer Insights shows a large number of 4 and 5-star reviews for the market as a whole.
- TrustRadius: IBM Verify scores an 8.1 out of 10 based on 92 reviews and ratings.
- Infotech: Gives a rating of 7.7 out of 10 from 7 reviews, with an 85% positive "Emotional Footprint" score. This suggests generally positive user feelings.
- Mobile App Stores: Specific combined star ratings for the IBM Security Verify mobile app were not found. However, individual user comments on Google Play mention some error reports and questions about usability.
Users consistently praise its strong security features (MFA, SSO, adaptive access). They also like its scalability as a complete platform for employee and customer identities, its deployment and connection flexibility for hybrid systems, and its automation features.
But, common weaknesses mentioned include the difficulty of setup, a user interface that some find old or complex, a steep learning curve, mobile app performance problems, and a pricing model that can be hard to predict.
Overall View of IBM Security Verify
A big reason people choose IBM Security Verify is that it can be used as both an IAM and a CIAM solution. This is not true for most platforms.
IBM Security Verify's strengths are in its wide range of functions. It covers SSO, varied MFA choices (including passwordless and FIDO2), advanced IGA, PAM, CIAM, and a sophisticated AI-powered adaptive access and risk engine that uses Trusteer technology.
Its design is made for complex on-site and multi-cloud systems, which is an essential need for many large businesses.
However, potential users should think about certain things. A common point in feedback is the potential difficulty in initial setup and deployment. This often requires specialized skills or professional services, which can affect the time it takes to see value and the TCO.
Infisign: The Best Alternative to IBM Security Verify
For a complete IAM and CIAM, Infisign gives both with its IAM Suite and UniFed. Besides this, it is built for businesses of all sizes, which means it gives access control to both startups and large companies.
With over 6000 API + SDK connections, Unlimited Directory Sync, and Advanced Features without hidden charges, Infisign is the best alternative to IBM Security Verify for security and automation. It also has:
- AI Access Assist: Going beyond backend risk analysis, AI Access Assist is a useful tool built to greatly lessen the administrative workload. Connecting with tools like Slack and Teams, it allows IT administrators to manage user access requests in under a minute.
- Attribute-Based Access Control (ABAC): Infisign gives precise and scalable control over user permissions through a flexible ABAC framework. This allows for quick, large-scale changes based on user attributes. It is a more dynamic and manageable alternative to working with complex policy engines.
- Universal SSO + Adaptive MFA: Infisign puts a high value on the user's experience by using Infisign’s Single Sign-On (SSO) with adaptive, user-friendly MFA options like biometrics. This attention to ease of use is different from platforms where the user interface can feel dated or mobile app performance is not consistent.
- Just In Time Access: Infisign makes it simple to apply the principle of least privilege with fully auditable Just-In-Time access. This feature allows users to get temporary, higher permissions only when needed.
- Automated User Provisioning: This approach is designed for quick setup. It helps companies secure user access from day one without the long, complex configuration projects often needed to set up automation in older IAM platforms.
- Supports Access Across Multiple Ecosystems: With a huge library of pre-built connections, Infisign is built for simple connection across different IT systems. This includes old apps that do not support SAML as well as on-site apps that are usually not reachable through the cloud.
Want to see Infisign in action? Book a free demo with our team!

IBM Security Verify FAQs
What is IBM Security Verify used for?
IBM Security Verify is a full Identity and Access Management (IAM) solutions suite. It is used to manage and secure identities (both employee and customer) and their access to digital materials across complex hybrid multicloud systems.
Is IBM Security Verify an Identity Provider (IdP)?
Yes, IBM Security Verify can work as an Identity Provider. Key parts like IBM Security Verify SaaS (once called IBM Cloud Identity) and IBM Security Verify Access (once called ISAM) supply core IdP abilities. They support open standards such as OpenID Connect (OIDC) and SAML 2.0.
What are the deployment options for IBM Security Verify?
IBM Security Verify gives flexible deployment choices to fit different business needs. The suite supports fully cloud-based (SaaS) setups and on-site installations (often as virtual or hardware appliances for parts like Verify Access and Verify Governance). It also supports hybrid-cloud setups that mix both cloud and on-site elements.