Future-ready firms treat identity like electricity and biometric authentication methods are the switch. Leaders plug every door laptop and app into live face, voice or palm data to stop ninety percent of fraud before it starts. Workers skip passwords and move straight to value work while the system logs each entry with court-ready proof.
The firm keeps no central vault of prints or faces so privacy risk drops near zero. Clean, touch-free readers remove shared surfaces, and cost per login falls below one cent. Only invited people pass each gate so trade secrets stay inside and partners trust the brand. Lines vanish, output rises and users leave with a smile.
What Is Biometric Authentication?
Biometric authentication is simply a way of confirming who you are by using unique traits of your body or behavior. A password is what you know. A card or token is what you have. Biometrics are what you are.
The system works like this. First you enroll by giving a sample such as a fingerprint or face scan. The system then creates a digital template from that sample. Later when you log in it compares your live sample to the stored template. If they match you get access. This happens in milliseconds.
There are two main types of biometrics. Physical biometrics look at your body such as fingerprints or eyes or face. Behavioral biometrics look at patterns of action such as typing style or walking or speaking.
Benefits of Biometric Authentication
Biometric systems turn security into a profit line. They cut fraud losses to near zero because every login links to one living person. Once biometric authentication methods go live, the daily routine changes in small but measurable ways. Let us see how the next points turn these quiet wins into hard numbers.
Enhanced Security and Fraud Prevention
- Biometric traits are very hard to copy. A fingerprint is yours alone. A face pattern is unique. This makes it much stronger than passwords which can be stolen or guessed.
- Many banks that adopted biometric authentication methods have seen big drops in fraud and account takeovers.
Improved User Experience and Convenience
- You do not forget your fingerprint. You do not forget your face. This makes biometrics easier and faster for users compared to passwords. People prefer it because it feels natural.
Cost Reduction and Efficiency
- Password resets cost money. Every time an employee calls IT for a reset it can cost up to 70 dollars. Biometrics cut that problem out. They also reduce manual checks in banks or hospitals which saves time and resources.
Non-Repudiation and Accountability
- When a biometric is used there is a clear link to the person. You cannot later deny it was you. This helps with audits and compliance and fraud detection.
Contactless and Hygienic
- After the pandemic contactless solutions became more important. Biometrics like face or iris scans allow secure logins without touching surfaces.
10+ Types of Biometric Authentication Methods
Now let us go through the main types of biometric authentication. We will look at how they work and their pros and cons and where they are used. You will see that each method has its own strengths depending on what you need.
Physiological (Physical) Biometrics
Physical biometrics focus on traits your body naturally has. These traits stay mostly the same throughout your life which makes them reliable for long-term use. Let me walk you through the most important ones.
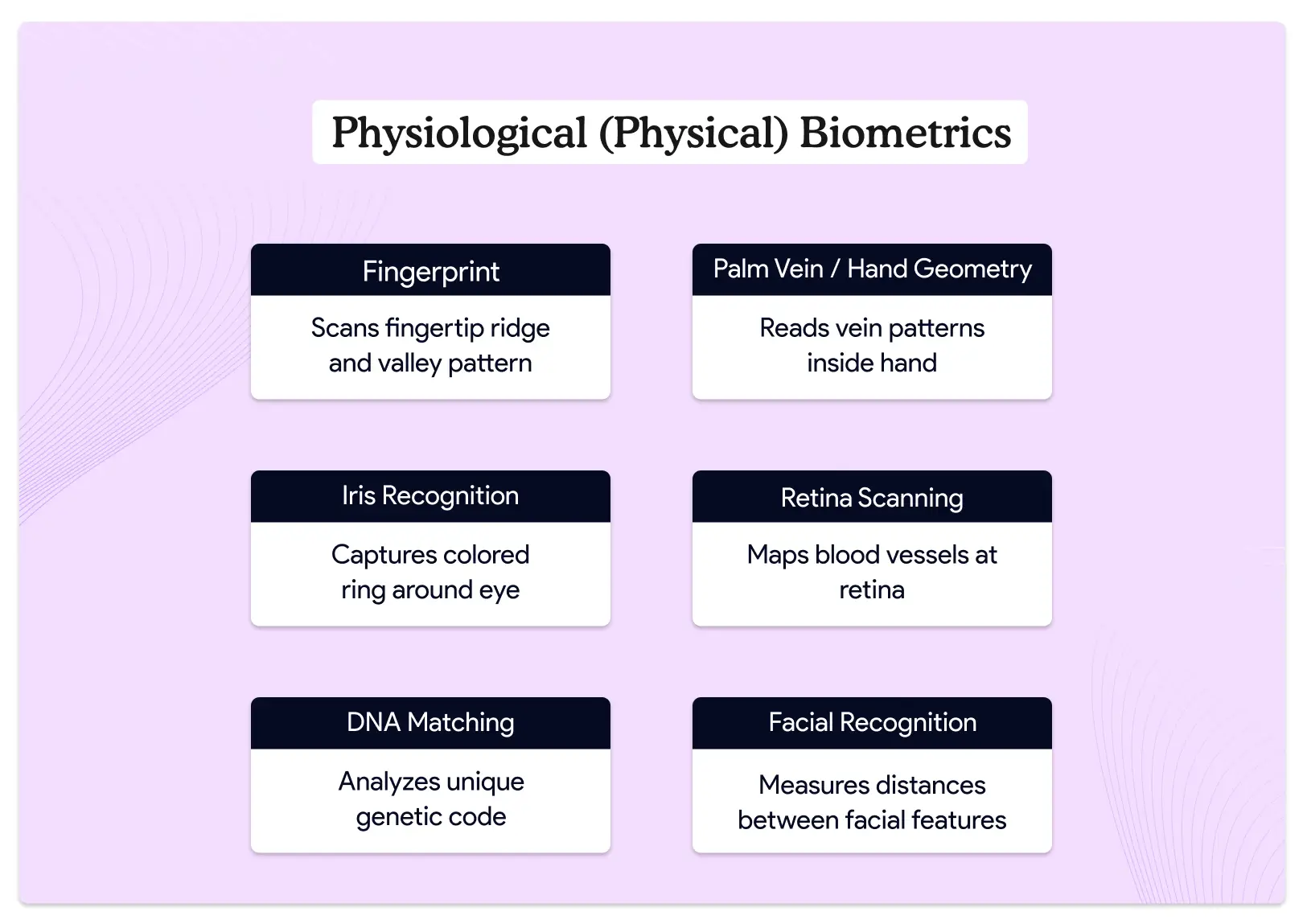
Fingerprint Recognition
Fingerprint recognition records the ridge and valley pattern of a fingertip and converts it into a digital template. The reader compares this template with the live scan in under one second and grants access only when both match.
Pros
- Very accurate with quick response time usually under one second
- Works on most devices without extra hardware making it cheap and practical
- Users are familiar with it and usually find it easy to accept
- Technology is mature and widely deployed across industries
Cons
- Can be tricked with fake or lifted fingerprints in some cases
- Injuries, burns or dirt can affect recognition accuracy
- Requires physical touch which can raise hygiene concerns
- Fingerprint cannot be changed once compromised
Use Case:
- Shops let buyers pay by pressing a finger to the card terminal so the sale finishes in one second and no one types a PIN.
- Office staff open doors with the same press and the building log shows who entered and when.
Palm Vein or Hand Geometry
Palm vein scan looks at the blood lines inside your hand. It needs a live heart beat so a fake hand or photo will not work. The reader sits on a desk and the user just holds the hand over it for one second.
Pros
- Extremely secure because vein patterns are hidden and require blood flow
- Contactless so safe and hygienic
- Very accurate with low false matches
- Not affected by dirt or scars or surface issues
Cons
- Needs special infrared scanners which are costly
- Not as common or familiar to people as fingerprints or face
- Some medical or circulation issues can impact accuracy
Use Case:
- A nurse rests her palm over the reader and the drug cupboard opens for her shift and no one else can enter. After the 2011 quake Japanese banks added palm readers at ATMs so customers can take out cash even if they leave the card at home
Iris Recognition
Iris authentication takes a picture of the colored ring around your eye. The camera sees more than two hundred unique points that stay the same from childhood to old age. The scan works in one second and needs no touch so users only look at a small lens.
Pros
- Extremely accurate and reliable even more than fingerprints
- Contactless and works from a short distance
- Very hard to fake or replicate
- Works with glasses and contact lenses
Cons
- Needs special cameras so higher setup cost
- Some people feel uncomfortable being scanned in the eye
- Certain eye diseases may affect accuracy
Use Case:
- A traveler stands still for one second and the gate opens.
- The airport camera has matched her iris to the ticket and no one touches a keypad.
- Police vans scan eyes at roadside checks and match them in seconds to find missing persons or flagged suspects.
Retina Scanning
Retina scanning shines a safe light at the back of your eye. It maps the blood vessel pattern which is unique to every person and never changes. The scan takes two seconds and needs the eye to be very close to the lens.
Pros
- Almost perfect accuracy with extremely low error rate
- Very stable pattern that does not change easily
- Impossible to forge since it is internal
Cons
- Requires very close eye scans which feel uncomfortable
- Expensive equipment and slow enrollment process
- Not suitable for everyday or mass use
Use Case:
- A soldier leans into an eyepiece and the gate of a secure arms store opens after the device maps the blood vessel pattern at the back of his eye in two seconds .
- A few Japanese banks have tested retinal readers at ATMs so customers can withdraw cash even if they forget the card at home .
DNA Matching
DNA matching reads the genetic code inside a tiny drop of blood or saliva. The sequence is unique to each person except identical twins. Lab machines need hours to process the sample so the result is not instant.
Pros
- Highest level of uniqueness possible among all biometrics
- Can confirm identity even from very small samples
- Stays the same throughout life
Cons
- Not usable for real-time login since processing takes time
- Needs physical sample collection and costly equipment
- Privacy concerns are very high with DNA data
Use Case:
- Forensic teams compare this code to crime-scene samples to confirm a suspect in days.
- Family-history sites also use the same process to link long-lost relatives who share matching segments.
Facial Recognition
Facial recognition measures the distance between eyes, nose and jaw. A small camera takes the picture and the software checks it in under one second. The scan works from a short distance and needs no touch. Facial biometric authentication has become popular because it works fast and feels natural.
Pros
- Contactless and works at a distance without effort from user
- Very fast often under a second
- Already supported on many phones and laptops with normal cameras
- Can identify people in crowds for surveillance
Cons
- Can be tricked with photos or videos or masks if liveness checks are weak
- Accuracy depends on lighting and angle of face
- Concerns about bias and privacy are common
- Susceptible to deepfake attacks
Use Case:
- A passenger walks toward the gate and the camera on the post scans her face in one second.
- The system matches the image to her passport photo and the gate opens without a ticket check.
- In the city metro the same camera watches the platform and alerts staff if a missing child appears on the feed.
Behavioral Biometrics
Behavioral biometrics watch how you act, not how you look. The system notes your typing speed, mouse path and phone swipe rhythm. It keeps checking in the background and spots a stranger in seconds. Banks and online tests use this method because it needs no new sensor and never disturbs the user.
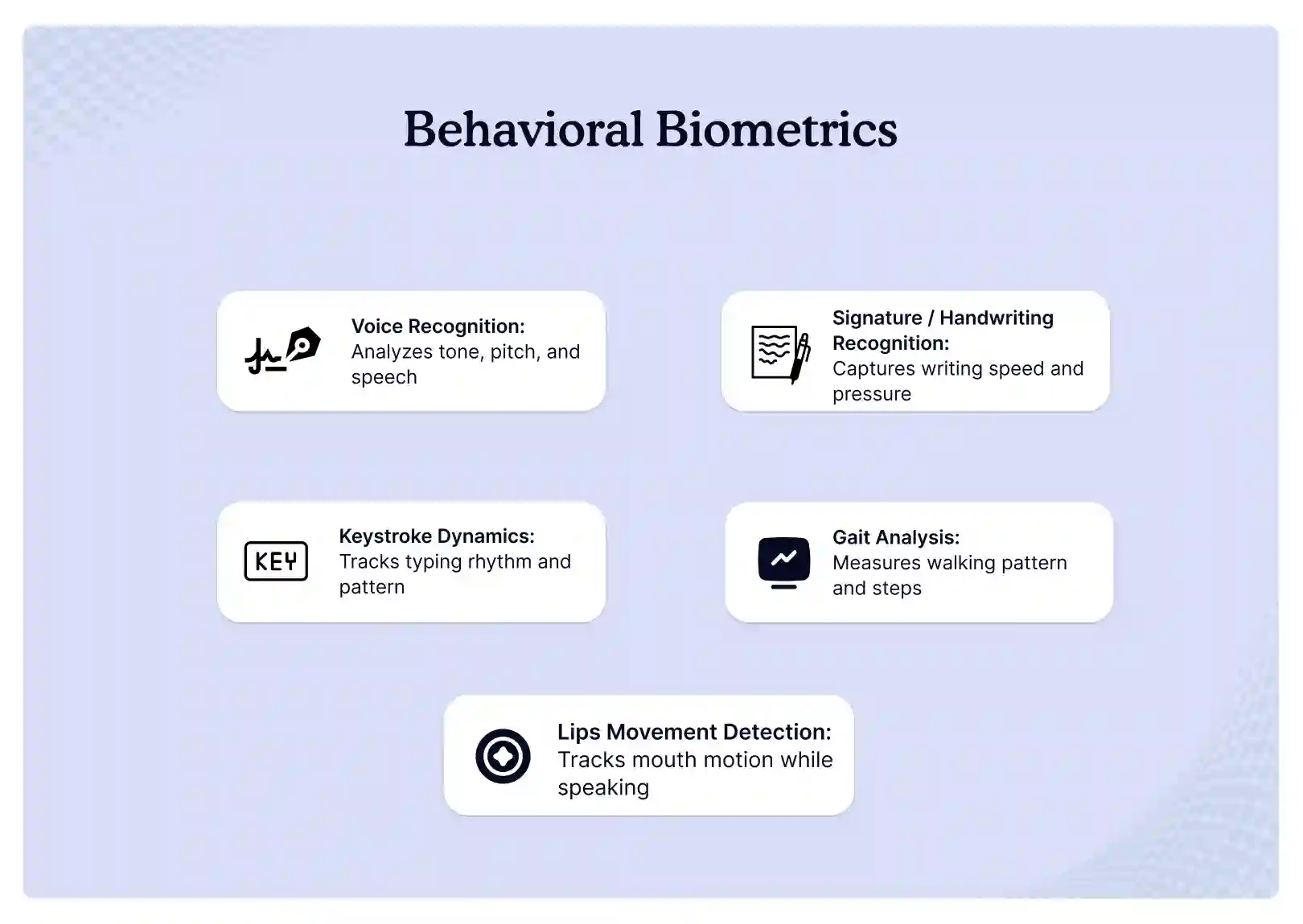
Voice Recognition
This method creates a voiceprint from your tone and pitch and speech style. Voice biometric authentication is especially useful when you need hands-free access.
Pros
- Works over phone or microphone without special tools
- Convenient for remote users and hands-free systems
- Familiar and natural for most people
Cons
- Background noise or illness can reduce accuracy
- Can be recorded and replayed by attackers
- Deepfake voice technology is a growing threat
Use Case:
- A bank app watches how you tap and swipe on your phone. If the speed or rhythm changes the app asks for extra proof.
- A call centre does the same while you type so a stolen password is not enough to get in.
Signature/Handwriting Recognition
Signature recognition records the speed, pressure and angle of your pen. It cares more about how you sign than how the letters look. The data is taken by a special pad or a phone screen.
Pros
- Already legally accepted in many places
- Familiar and low resistance from users
- Captures behavioral traits that are hard to copy exactly
Cons
- Natural variations in signature lower accuracy
- Can still be forged with enough practice
- Not suitable for continuous authentication
Use Case:
- A courier hands over a tablet and the customer signs on the screen. The pad records the speed and pressure of the pen and checks it against the sample on file. If the numbers match the package is delivered and the driver moves to the next stop.
Keystroke Dynamics
Keystroke dynamics counts the time between each key press and release. The rhythm is unique to every user and is captured by normal software. The check runs in the background during any typing task. Schools and call centers use this method because it needs no extra hardware and keeps watching while work goes on.
Pros
- Needs no extra hardware only software
- Can run in the background for continuous monitoring
- Inexpensive and easy to deploy
Cons
- Accuracy is lower than physical biometrics
- Patterns change with mood or tiredness or injury
- Different keyboards can affect consistency
Use Case:
- A student logs in to an online exam site and starts typing. The site records how long each key is pressed and the pause between letters. If the pattern differs from past samples the test is paused and a live proctor steps in to check identity.
Gait Analysis
Gait analysis measures how you walk. It looks at step length, speed and sway. A camera on the ceiling records your motion and the software builds a pattern.
Pros
- Works at a distance without any cooperation
- Hard for a person to consciously change gait
- Can be used in surveillance without face capture
Cons
- Accuracy is low compared to other biometrics
- Footwear or injuries or environment can change walking pattern
- Mainly useful for identification not secure login
Use Case:
- A security camera above the store entrance measures how fast and wide each person walks. If the pattern matches a banned shopper the guard gets a silent alert and walks over. The system works without asking anyone to stop or show a card.
Lips Movement Detection
Lips movement detection watches how your mouth moves when you speak. A small camera tracks the shape and speed of each motion. The system compares these moves to the words it hears. If the timing does not match it knows the voice may be fake.
Pros
- Strong protection against photo or video spoofing
- Requires live speech so natural liveness detection
- Works well with voice recognition in multi-factor setups
Cons
- Needs clear camera view of lips
- Facial hair or lighting can reduce performance
- Still new and not widely deployed
Use Case:
- A bank call-centre camera checks that lip motion matches spoken words so a deepfake voice is rejected even if it sounds right.
- Car makers test in-cab lenses that watch lip edges so voice commands work in loud traffic without grabbing the wheel.
- Police pull silent CCTV clips and read the words from lip motion to learn what a suspect said during a crime.
How to Choose the Right Biometric Authentication Method?
There is no single best sensor. The right choice is the one that keeps risk low users happy and the budget intact. You must think about what you guard, who will use it and how much you can spend before you pick a trait.
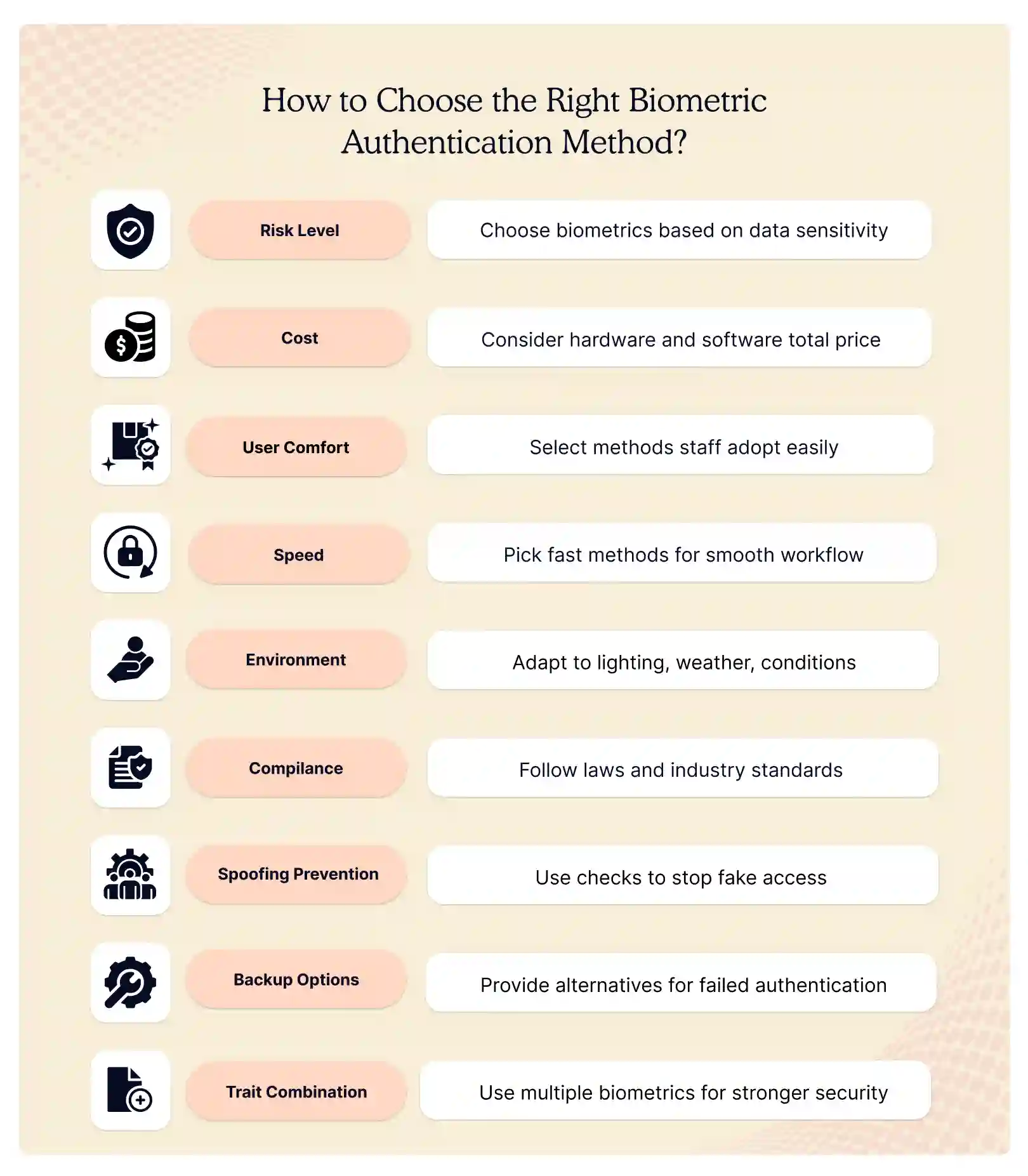
- Risk Level. High value data vaults need two strong traits such as iris plus card. General office doors can run on one fast trait such as face or finger. Low value areas may stay on badge only.
- Cost. Face and voice run on any phone so the hardware bill is tiny. Iris, palm, vein, and retina need special cameras and raise the price per gate. Count both the reader and the server licence before you decide.
- User Comfort. Staff adopt finger and face quickly because phones taught them. Retina and DNA feel slow or intrusive so run a pilot first. Ask workers to test the sensor for a week and watch the drop in daily logins.
- Speed. Fingers and face finish in under one second so queues stay short. DNA and retina take minutes so reserve them for rare high trust checks such as vault access or court proof.
- Environment. Wet hands break finger reads so factory lines prefer palm vein. Bright sun hurts face reads so add a shade or switch to voice. Cold plants that need gloves may choose iris over touch based traits.
- Rules. HIPAA wards need full audit trails so pair biometrics with signed logs. PCI-DSS cages need two factors so add a card or PIN. Check local privacy laws before you store any template.
- Spoof Risk. Use liveness checks on face and voice to beat deepfakes. Use blood flow checks on the palm and finger to beat fake prints. Update the firmware every quarter to keep pace with new attack tools.
- Fallback. Always keep a second trait or a one time code ready for broken fingers, lost voice or mask day. Print a backup QR code for visitors and keep the help desk number visible. A bank may combine two biometric authentication methods for better fraud protection.
- Mix. The safest path is face plus finger or iris plus card. If one trait fails the second still lets the right person in and keeps the workflow alive.
Challenges & Considerations of Biometric Authentication
Biometrics cut risk but they bring new duties. A template is not a password and a sensor is not magic. Plan for theft bias cost and law before you roll out any trait.
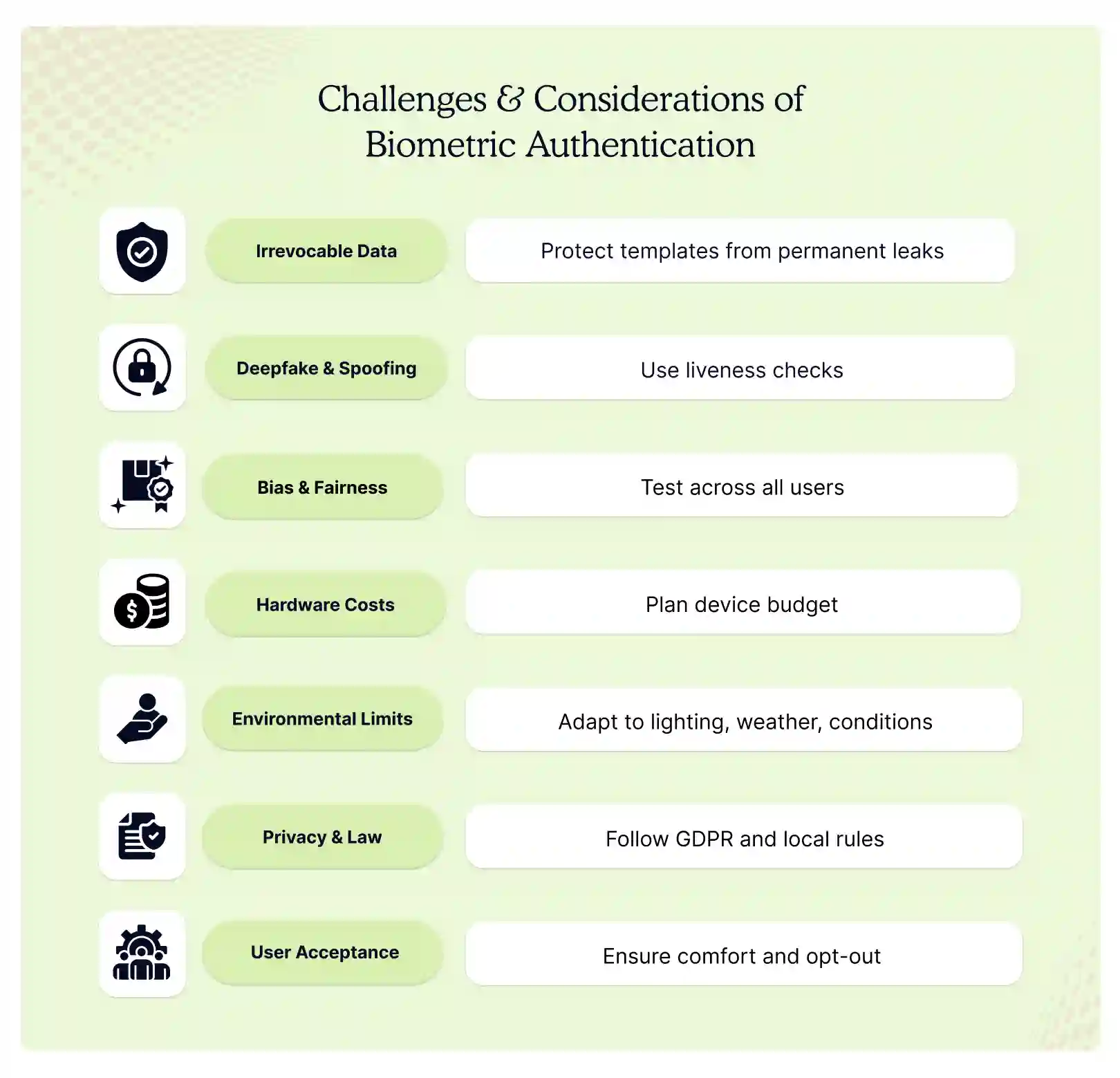
- Irrevocable Data. If a fingerprint template leaks the user cannot grow a new finger. Store salted hashes and keep the raw image off any network to limit the blast radius.
- Deepfake and Spoofing. Cheap apps now make a face or voice say anything. Run liveness checks such as eye blink depth texture or heartbeat in palm scans to stop replay attacks.
- Bias and Fairness. Some face systems fail more on darker skin and voice systems drop accuracy for older users. Test every new release across age, gender and ethnicity and keep a human review step for edge cases.
- Cost of Hardware. Iris and palm-vein cameras cost five to ten times more than finger units. Start with high-risk doors and expand in phases so the budget keeps pace with the proof of value.
- Environment Limits. Bright sun blinds iris cameras and wet hands break fingerprint reads. Place sensors under shade and offer dry-wipe stations or add a second trait such as voice for monsoon days.
- Privacy and Law. GDPR calls biometric data a special category and India’s DPDP Act demands explicit consent. Store templates on user devices when possible and run a privacy impact study before any cloud upload.
- User Acceptance. Some staff fear eye scans or worry about disease from touch pads. Run open demos, publish data sheets and give an opt-out path with a secure badge to keep trust high.
Plan Your Future-Ready Biometric Architecture with Infisign
Building a strong biometric system isn't just about fancy hardware. By 2026 businesses need a platform that keeps things safe, private and easy for users. Infisign gives you all that with its smart Zero Trust approach.
Here is why Infisign is a great choice
- Zero Trust Framework. Every access request gets checked. We don't just trust anyone automatically. User identity, device health, and location are all verified before access is allowed. This helps stop hackers from moving around inside your system.
- Passwordless Biometric Integration. Infisign passwordless authentication removes the need for passwords. Users log in with biometrics such as fingerprint, facial recognition or iris scans. The platform supports over six thousand applications and the login process completes in seconds. Companies that deploy the service record a fifty percent drop in password-related tickets. The iris code that is obtained is then scrambled for safety reasons and this scrambled code is kept safely in the Infisign Vault.
- Decentralized Identity Architecture. Users own their own biometric info. Data stays encrypted on their devices instead of on a central server. This means no single point of failure for hackers to target.
- Anti Spoofing with Liveness Detection. Infisign can tell fake faces or deepfakes from the real thing. It watches for unusual behavior in real time to stop breaches before they happen.
- Cryptographic Key Management. Biometric data gets turned into super secure cryptographic keys. Hackers can't reverse engineer them so your data stays safe.
- Seamless SSO and Lifecycle Management. You can connect biometrics to over 6000+ apps in just a few hours. Onboarding and offboarding users is easy with AI powered workflows.
- Compliance Ready Audit Trails. Detailed logs show who accessed, what, when, and from where. This helps with GDPR HIPAA and PCI DSS rules.
Infisign turns biometric authentication from a vulnerability into your strongest defense layer. Consider exploring passwordless authentication as part of your strategy. You also need the right identity and access management software to manage all these biometric authentication methods effectively.
Ready to build your future-proof biometric security architecture? Schedule a demo with Infisign today and see how enterprises are protecting their critical assets with next-generation authentication.
FAQs
Which is safer: biometric or password?
Biometrics are generally much safer than passwords alone. Passwords can be easily guessed or phished or stolen through data breaches. Biometric traits are unique and nearly impossible to replicate.
However the safest approach combines both methods. Biometrics provide something you are and passwords represent something you know. Together they create layered security that is very hard to break.
What are the advantages and disadvantages of face biometrics?
Face biometrics are contactless and fast and work at a distance. They are already built into many phones and laptops which makes them convenient and familiar.
But they can be tricked with photos or videos or masks if the system does not have good liveness detection. Accuracy also depends on lighting and angle. Privacy concerns are real especially when used for surveillance.
What are the disadvantages of biometric authentication?
- The biggest disadvantage is that biometric data cannot be changed once compromised. If someone steals your fingerprint data you cannot get a new fingerprint.
- Other issues include implementation costs and false acceptance or rejection rates and vulnerability to deepfakes and privacy concerns. Some systems also show bias across different demographic groups.
What is the main advantage of using biometrics in MFA?
- The main advantage is combining maximum security with user convenience.
- Biometrics represent something you are which is inherently tied to you and cannot be forgotten or lost or easily transferred to attackers.
- When combined with other factors like passwords or tokens, biometrics create layered security that is much harder to breach. An attacker would need to compromise multiple factors at once which is extremely difficult.
Is biometrics more secure than OTP?
Both have their strengths. Biometrics cannot be phished or intercepted in transit and are inherently tied to you. OTPs can be easily revoked and regenerated if compromised.
For maximum security the ideal approach combines both. Use biometrics as the primary authentication factor and supplement with OTP for critical operations or high-risk scenarios. This hybrid model gives you the best of both worlds.




























