Enterprise security has fundamentally changed. Remote workforces doubled since 2020. Traditional perimeter defenses no longer apply when employees access systems from anywhere.
Identity attacks now dominate the threat landscape. 81% of data breaches involve compromised credentials. Organizations lose $4.45 million per incident on average. Password management alone costs companies $480 per employee annually.
This guide covers 11 best-in-class enterprise access management solutions. They address current identity issues and provide strong security for distributed organizations.
Best Enterprise Access Management Solutions
What Are Enterprise Access Management Solutions?
Enterprise access management solutions are platforms that control who accesses your digital systems. They verify each user's identity before granting access. They enforce security policies across your applications and databases. They track every access event in your network. This gives you complete control over your company's digital resources.
These solutions work as master keys for your digital workplace. They manage passwords and control access to apps. They also track what people do online.
Here are the key parts that make these systems work:
- User Identity Management. The system creates digital profiles for every person. It handles user provisioning when people join. It handles deprovisioning when people leave. It knows who they are and what job they do.
- Authentication Methods. These check that people are who they say they are. This includes passwords, fingerprints, and face scans. It also includes phone codes that prove identity.
- Access Control Policies. The system follows rules about who can access what. These rules change based on job roles and time. They also change based on security needs.
- Single Sign-On Capabilities. Users log in once and get access to all apps. This makes work faster and reduces password problems.
- Monitoring and Reporting. The system watches all access activity. It creates reports that help you spot problems. These reports also help prove you follow security rules.
- Centralized User Control. You manage all users from one place. You control access across all your apps and systems.
- Compliance and Audit. The system helps you meet legal rules. It creates audit trails for investigations.
- API & SDK Access. Developers can connect the system to your apps. They can build custom solutions for your needs.
Top 11 Enterprise Access Management Solutions in 2026
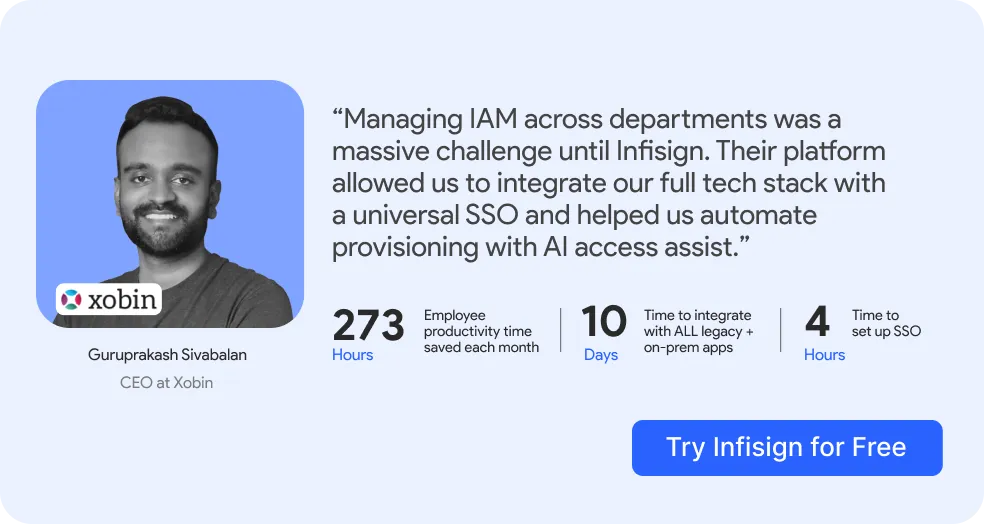
1. Infisign
Your enterprise access management infrastructure faces critical vulnerabilities. Traditional IAM solutions cannot address these problems. 90% of organizations experienced identity breaches because legacy systems use centralized databases. These create single failure points and expose systems to attacks.
Infisign delivers enterprise access management solutions through passwordless authentication. It follows zero trust IAM architecture. This solution eliminates password vulnerabilities using continuous verification protocols.
Key features:
- Centralized Access Management. You control all user access from one place. You manage permissions across all your apps and systems.
- Access Control Policies (RBAC & ABAC). Role-based access control gives users permissions based on job roles. Attribute-based access control uses multiple factors for decisions. Location, time, and device status determine access.
- Universal SSO. Users log in once and access all apps. This saves time and reduces password problems.
- IT Access Reviews. Regular reviews check if users have correct permissions. You remove access that people don't need anymore.
- AI Access Assist: With AI access assist, you grant access to users using AI to authenticate based on your set policies, or by requesting access on platforms on Slack or Teams, making things a lot quicker.
- Non-Human Identities. The system manages access for apps and services. It also manages devices that connect to your systems.
- API Integrations. Developers can connect Infisign to any app. Over 6000+ pre-built integrations work out of the box.
- Compliance and Audit Management. It ensures compliance with standards like HIPAA and GDPR by providing automated access logs and real-time audit trails.
- Zero Trust Architecture. Every access request gets checked no matter what. This happens regardless of user location or device. This approach protects against external attacks and insider threats.
- Reusable Identity Technology. Users create one secure identity that works everywhere. This reduces the need for multiple passwords. It also improves security at the same time.
How Infisign Unified Multiple IdPs for a Global Manufacturing Giant
Infisign acts as a central identity gateway for one of our MAJOR manufacturing clients’ fragmented identity landscape. We removed productivity bottlenecks, security risks, and EXPENSIVE delays.
Infisign unifies the entire ecosystem, bridging disparate directories and tools without replacing costly legacy infrastructure.
How Infisign Helped Our Leading Manufacturing Client:
- Shattered Identity Silos: Created a single source of truth by syncing with all existing IdPs (like Azure AD, Cognito), instantly bridging disparate systems.
- Universal Single Sign-On (SSO) Experience: Delivered a true Single Sign-On experience, authenticating users once for secure, immediate access to every application they need.
- Effortless Legacy App Access: Wrapped decades-old, on-premise applications in a zero-trust security framework, removing vulnerabilities without rewriting a single line of code.

Pros:
- Eliminates password-related security risks
- Reduces authentication costs by 60%
- Works with 6000+ applications
- Zero trust security model
- AI-powered threat detection
Cons:
- Passwordless authentication requires the use of its encrypted password vault feature.
2. Okta Workforce Identity
Okta provides cloud-based identity and access management. This platform connects cloud applications well. It provides smooth user experiences through a comprehensive enterprise access control system.
The solution works for medium to large companies. It works for businesses that use many cloud applications.
Key features:
- App Integration. Okta connects with many pre-built applications. It supports custom integrations for unique business needs.
- Lifecycle Management. User setup and removal happens without manual work. This ensures people get right access when they join. They lose access when they leave.
- API-First Architecture. Developers can integrate Okta into existing applications with some effort. They can also build custom identity solutions.
- Reporting Capabilities. Analytics help you understand access patterns. They help identify security risks across your organization.
Pros:
- Strong app marketplace with 7000+ integrations
- Mature platform with proven track record
- Good developer tools and APIs
- Strong customer support
Cons:
- Can be expensive for smaller organizations
- Complex pricing structure
- Some advanced features require additional licenses
3. Ping Identity
Ping Identity works with advanced authentication methods and hybrid cloud setups. This solution serves large companies with infrastructure needs seeking enterprise access management solutions. The platform handles both cloud and on-site systems.
Key features:
- Hybrid Deployment Options. The solution works across cloud and on-site environments. It doesn't need major infrastructure changes.
- Risk-Based Authentication. Learning algorithms check the risk of each access attempt.
- Developer-Friendly APIs. APIs and SDKs make integration possible. You can add identity services to custom applications and workflows.
- Scalable Architecture. The platform handles many authentication events. It maintains response times and availability.
- Fraud Detection Capabilities. Built-in fraud detection finds unauthorized access attempts. It prevents them before they succeed.
Pros:
- Excellent for hybrid environments
- Strong fraud detection capabilities
- Handles high-volume transactions
- Good for complex enterprise needs
Cons:
- Steep learning curve for administrators
- Higher implementation costs
- May be overly complex for simple use cases
4. JumpCloud
JumpCloud offers cloud-based directory services. These replace traditional Active Directory systems. This solution works for small to medium businesses seeking enterprise access control solutions. It provides simple identity management.
The platform gives central control over users, devices, and applications.
Key features:
- Cloud Directory Services. Central user management works across Windows, Mac, and Linux systems. It doesn't need on-site infrastructure.
- Device Management Integration. Control and secure all company devices from one platform. This same platform manages user identities and access.
- Multi-Factor Authentication. Built-in multi-factor authentication protects against password attacks. It stops unauthorized access.
- Simple Pricing Model. Per-user pricing makes budgeting workable. It's simple to scale as your organization grows.
Pros:
- Easy to set up and manage
- Good for mixed device environments
- Transparent pricing
- No on-premises infrastructure needed
Cons:
- Limited advanced features compared to enterprise solutions
- Fewer third-party integrations
- May not scale well for very large organizations
5. OneLogin
OneLogin focuses on single sign-on and user setup for cloud-first organizations. The platform helps firms upgrade from legacy office systems to cloud identity platforms.
The platform connects different applications well. It automates user management tasks.
Key features:
- User Setup. User provisioning and deprovisioning happens without manual work. This depends on HR system changes and access policies.
- Mobile Application Support. Native mobile apps provide secure access to company resources. This works from smartphones and tablets.
- Real-Time Security Monitoring. Continuous monitoring finds suspicious activities. It detects potential security threats as they happen.
- Deployment Options. Choose cloud, on-site, or hybrid deployment. Your security and compliance needs determine this choice.
Pros:
- Strong SSO capabilities
- Good mobile support
- Competitive pricing
- Easy cloud migration tools
Cons:
- Limited advanced security features
- Smaller app catalog than competitors
- Customer support can be inconsistent
6. SecureAuth
SecureAuth provides flexible authentication and risk-based access control. The platform serves organizations needing strong security measures and smart threat detection . The platform uses behavioral analytics to find potential security threats.
Key features:
- Continuous Authentication. Users stay authenticated through ongoing verification. This is instead of single login events.
- Threat Intelligence Integration. Real-time threat feeds help identify known attackers. They also identify suspicious IP addresses.
- Passwordless Options. Support for biometric authentication and smart cards. Other passwordless methods improve security and user experience.
- Access Policies. Create detailed access rules using user attributes. Also use device status, location, and risk factors.
Pros:
- Advanced threat detection capabilities
- Strong adaptive authentication
- Good for high-security environments
- Flexible deployment options
Cons:
- Complex to configure and manage
- Higher cost than basic solutions
- Requires security expertise to optimize
7. IBM Security Verify
IBM Security Verify offers business-level identity services. It uses AI and automation features. This solution helps organizations with security needs who want enterprise access control solutions.
The platform combines identity management with security analytics.
Key features:
- AI-Powered Risk Assessment. Learning algorithms analyze access patterns. They identify potential security risks in real time.
- Enterprise Scalability. The platform handles many users and authentication events. It maintains performance levels.
- Privileged Access Management. Special controls for admin accounts and sensitive systems. These need extra security measures.
- Analytics and Reporting. Insights into user behavior and access patterns. Also security events across your organization.
Pros:
- Strong AI and analytics capabilities
- Excellent for large enterprises
- Comprehensive security features
- Good integration with IBM ecosystem
Cons:
- Complex implementation process
- High cost for full feature set
- May be overkill for smaller organizations
8. AWS Identity and Access Management
AWS IAM provides cloud-native identity services for Amazon Web Services infrastructure. This solution integrates deeply with AWS services and resources through enterprise access management solutions. The platform offers granular access control for cloud environments.
Organizations using AWS infrastructure get native integration benefits. The service provides fine-grained permissions and security controls.
Key features:
- Native AWS Integration. Integration with all AWS services. This provides security controls across your cloud infrastructure.
- Policy-Based Access Control. Policy-based access control allows definition of access rules. You can define who can access which resources and when.
- Temporary Credentials. Security Token Service provides short-term access credentials. This reduces the risk of credential compromise.
Pros:
- Free with AWS account
- Deep AWS integration
- Granular permission controls
- Scales automatically with usage
Cons:
- Limited to AWS ecosystem
- Complex policy language
- No built-in SSO for third-party apps
9. Acquia
Acquia offers cloud-based identity services for customer-facing apps and digital experiences. This solution serves companies that manage public websites and customer portals.
The platform specializes in customer identity and access management needs.
Key features:
- Customer Identity Focus. Features for managing customer accounts and preferences. Also access to digital services.
- Social Identity Integration. Allow customers to log in using social media accounts. Maintain security and privacy.
- Progressive Profiling. Collect customer information over time. No need for lengthy registration forms.
- Marketing Integration. Connect identity data with marketing tools. Create personalized customer experiences.
Pros:
- Specialized for customer identity
- Good social login options
- Marketing tool integrations
- Scalable for high-volume customer bases
Cons:
- Limited workforce identity features
- Focused mainly on web applications
- Higher cost for advanced features
10. SailPoint
SailPoint focuses on identity governance and access certification. This works for large enterprises seeking enterprise access management solutions. This solution helps organizations maintain compliance and reduce access-related risks.
The platform provides complete visibility into user access across all systems.
Key features:
- Access Certification Campaigns. Regular reviews of user access. This ensures people have the right permissions for their current roles.
- Role-Based Access Control. Access management through predefined roles. These match job functions and responsibilities.
- Separation of Duties Controls. Prevent conflicts of interest. Ensure users cannot have incompatible access combinations.
- Analytics. Learning technology identifies access anomalies and potential security risks. This happens before they become problems.
Pros:
- Strong governance and compliance features
- Excellent for large enterprises
- Advanced analytics capabilities
- Good regulatory compliance support
Cons:
- Complex to implement and manage
- High cost and long implementation time
- May be overly complex for simple use cases
11. Microsoft Entra ID (Azure AD)
Microsoft Entra ID provides comprehensive cloud-based identity services. The platform integrates with Microsoft 365 and Azure services. This solution serves organizations heavily invested in Microsoft technology seeking integrated enterprise access management solutions.
The platform offers complete identity management for Microsoft-centric environments. It provides hybrid identity capabilities for cloud and on-premises integration.
Key features:
- Microsoft Ecosystem Integration. Integration with Microsoft 365 and Azure. Also works with on-site Active Directory for user experiences.
- Conditional Access Policies. Access rules using user, device, and location. Also application risk factors.
- Hybrid Identity Support. Connect cloud and on-site identities. This helps organizations moving to the cloud.
- Security Features. Built-in threat detection and identity protection. Security reporting across the Microsoft ecosystem.
Pros:
- Excellent Microsoft integration
- Competitive pricing for Microsoft customers
- Strong hybrid capabilities
- Good security features
Cons:
- Best value only within Microsoft ecosystem
- Limited third-party integrations
- Can be complex for non-Microsoft environments
Why Are Enterprise Access Management Solutions Important?
Your business faces credential-based attacks daily. 38% of breaches involve stolen passwords. Top stolen passwords include '123456' and 'password'. Remote work expanded attack surfaces. Cybercrime costs companies $8 trillion annually.
Traditional passwords don't work against modern attacks. Enterprise access management solutions solve this issue. They provide central identity management and advanced security.
Here are the main reasons why these systems help your business:
- Data Breach Prevention. These systems block 81% of credential-based attacks. Risk-based access control automatically evaluates login attempts using behavior patterns. Multi-layered security protects against insider threats.
- Regulatory Compliance. Meet GDPR, HIPAA, and SOX requirements automatically. Generate audit reports without extra work. An effective enterprise access control system maintains compliance across your growing organization effortlessly.
- Remote Work Security. Secure access from any location or device. Control data access for distributed teams. Scalability features ensure protection grows with your expanding workforce.
- Cost Reduction. Reduce password reset costs by 60%. Eliminate IT help desk tickets. Lower authentication infrastructure expenses while improving security posture.
- Productivity Improvement. Single sign-on eliminates password friction. Employees focus on work instead of login issues. Streamlined access boosts team efficiency significantly.
- Audit Trail Creation. Track every access event automatically. Create detailed investigation reports. Prove compliance to auditors with comprehensive activity logs.
What to Look for in an Enterprise Access Management Solution
Choosing the right enterprise identity authentication solutions needs careful thought. You need to look at your specific business needs and security requirements. The wrong choice can create security gaps. It can also make work harder for your employees.
Your decision should focus on features that solve your current problems. It should also support future growth.
Here are the key things to check when picking an enterprise access management solution:
- Security Architecture. Look for solutions that use modern security approaches like zero trust and continuous authentication. These approaches check every access request instead of relying on network perimeters. Choose solutions that verify users based on multiple factors. Location, device health, and behavior patterns should influence access decisions.
- Integration Capabilities. Make sure the solution connects with your existing applications, HR systems, and security tools. Check for pre-built connectors to popular business apps. Verify that APIs allow custom integrations. The solution shouldn't require major changes to your current infrastructure.
- User Experience Design. Choose solutions that make work easier for your employees instead of creating barriers. Look for single sign-on capabilities that reduce login friction. Test the mobile experience for remote workers. Simple interfaces reduce training time and support tickets.
- Scalability and Performance. Pick platforms that can grow with your organization without performance problems. Check how the solution handles peak usage periods. Verify that response times stay fast as you add more users. Cloud-based solutions often scale better than on-premises systems.
- Compliance Support. Check that the solution helps you meet industry regulations like GDPR, HIPAA, or SOX. Look for built-in audit trails and compliance reporting features. Verify that the vendor maintains security certifications. The solution should generate reports that auditors accept.
- Implementation and Support. Consider how complex deployment will be for your IT team. Check if the vendor provides implementation services and training. Look at support response times and available support channels. Read customer reviews about implementation experiences.
- Total Cost of Ownership. Look at all costs including licensing, implementation, training, and ongoing maintenance. Don't just compare upfront prices. Consider hidden costs like additional modules or professional services. Calculate the cost per user over several years.
- Vendor Stability and Roadmap. Choose vendors with strong financial positions and clear product development plans. Check how long the vendor has been in business. Look at their customer base and market position. Verify that their roadmap matches your long-term technology needs.
Mastering Enterprise Access Chaos with Infisign
Modern organizations struggle with identity chaos. Employees use dozens of applications and work from various locations.
Infisign's identity and access management platform changes this chaos into organized, secure access through innovative enterprise access management solutions. It protects your business while improving productivity.
Here's how Infisign solves these basic challenges:
- Passwordless Authentication Revolution. Infisign gets rid of passwords completely. It uses reusable digital identities that work across all systems. Users prove their identity once and get secure access everywhere.
- Zero Trust Security Implementation. Every access request gets checked no matter what. This happens regardless of user location or previous authentication. This approach protects against external attacks and insider threats.
- AI-Powered Threat Detection. The platform uses smart technology to learn normal access patterns. It detects unusual behavior that might show security threats.
- Application Integration. Connect with over 6000+ pre-built integrations. Use custom APIs to integrate with any application your business uses.
- Attribute-Based Access Control. Create smart access rules based on user attributes. Also use device status, location, time, and other factors.
- Non-Human Identity Management. Secure and manage access for applications and services. Also for devices that need to talk to your systems.
- Complete Compliance Support. Built-in features help you meet regulatory requirements. They maintain detailed audit trails for all access activities.
- Cost-Effective Implementation. Organizations reduce authentication costs by 60% with Infisign. They improve security and user satisfaction at the same time.
Ready to eliminate password chaos and strengthen your security? Contact Infisign today to see how passwordless authentication can transform your business operations while reducing costs by 60%.
FAQs
What is enterprise access management?
Enterprise access management controls access to organizational digital resources. These systems manage user identities and verify authentication. They enforce access policies and monitor activities. They protect applications, data, and systems from unauthorized access. They simplify work for authorized users.
How do enterprise access management solutions differ from IAM?
Enterprise access management solutions and IAM terms are often used similarly. But enterprise access management typically refers to complete solutions. These are designed for large organizations with complex needs. These enterprise solutions include additional features like advanced governance. They also have sophisticated compliance reporting. They have integration capabilities that serve specific requirements. These serve large-scale business operations.




























