Every modern business needs a strong and simple way to manage user security. Platforms like FusionAuth vs Auth0 help achieve this by offering secure login and access control systems for modern apps.
But they follow very different paths. One gives you full control and freedom to build your own system. The other offers ready tools that save time and effort.
The main question is which platform matches your goals in the best way. Understanding how both FusionAuth and Auth0 work will help you make a smart and safe choice for your security stack.
FusionAuth vs Auth0: A Detailed Comparison
What is FusionAuth?
FusionAuth is a CIAM platform built for developers. It handles user authentication and authorization for your customer-facing apps. Everything stays secure and flexible.
You get a single sign-on out of the box. Multi-factor authentication is built in. Passwordless login works smoothly. Social login integrates easily with providers like Google and Facebook.
You can deploy FusionAuth on your own infrastructure. Your user data stays on your servers. You control access policies and security configurations.
It supports OAuth2 for authorization. OpenID Connect handles authentication.
Your development team can integrate it quickly. Your end users get a fast, seamless login experience.
What is Auth0?
Auth0 is a popular platform among the identity and access management (IAM) tools that makes handling login and user security simple for any business. When comparing auth0 vs fusionauth, both offer secure and developer-friendly solutions but differ in how much control they give you.
Auth0 comes with ready-to-use login pages, multiple social login options, and powerful tools trusted by large enterprises. You can set it up for web apps and mobile apps and even older systems. Getting started is quick and you can have it running in just a few hours.
Auth0 helps you stay safe with login detection and password breach alerts that keep your accounts protected. It also shows clear details about how people use your app. It is a trusted tool that handles most of the security work for you so your team can focus on building the product.
FusionAuth lets you handle everything your own way and make every part fit your needs. In the FusionAuth vs Auth0 debate, this flexibility is what attracts developers who prefer control. Auth0 on the other hand gives you a ready system that just works so you can focus on building your product instead of managing logins.
Key Differences FusionAuth vs Auth0 (2025 Edition)
Key Features of FusionAuth vs Auth0
FusionAuth and Auth0 offer strong authentication tools but differ in control and ease. This is why many teams compare the two platforms side by side before deciding which one best fits their needs.
FusionAuth's Standout Features:
- Core System. FusionAuth is fast and built to scale. It runs on Java and works on your servers or in the cloud. It supports PostgreSQL and MySQL. Powerful APIs make setup and automation easy.
- Authentication Support. FusionAuth supports OAuth2, OpenID Connect, and SAML 2.0. It integrates smoothly with your tools so users can log in anywhere without hassle.
- Customization. You can change the look and flow of login and signup. Update emails and themes easily. Add your own logic with webhooks and APIs.
- Developer Friendly. FusionAuth has clear docs and SDKs for JavaScript, Python, Java, and .NET. Get started fast with the quick installer or Docker image.
- Security. It protects your system with multi-factor and passwordless login. Detailed logs and tracking keep everything secure.
Auth0's Standout Features:
- Universal Login. Auth0 uses a hosted Universal Login system that gives users one secure sign-in across all apps. The login page is customizable with themes and branding and supports WebAuthn and multi factor authentication.
- Identity Providers. Auth0 connects with both social and enterprise identity systems. It supports over thirty providers, including Google , Apple, and Facebook, as well as enterprise solutions like Active Directory and LDAP.
- Actions and Custom Logic. Developers can use Actions to add custom rules or connect external APIs at different points in the login process. This helps manage complex authentication flows without rewriting core logic.
- Single Sign On. SSO makes logging in simple. A user signs in once and gets instant access to all connected apps. It feels seamless like one door that opens to everything they need without extra steps or passwords.
- Passwordless Login. Auth0 supports magic links and one-time codes through email or SMS as well as biometric login using WebAuthn for a smoother and safer experience.
Authentication & Identity Features
FusionAuth and Auth0 both offer powerful authentication methods but differ in flexibility and setup. Their identity features highlight this difference clearly.
FusionAuth Authentication and Identity Features
- Custom Registration Forms. FusionAuth lets you design your own registration process. You choose what user details to collect, how to validate them and where to store the data.
- Authentication Options. It supports single sign-on and multi-factor authentication using SMS, email, authenticator apps, and biometrics. It also offers passwordless login through magic links or one time codes.
- Gaming Identity Support. FusionAuth can connect with gaming identity providers making it a strong choice for gaming platforms and related applications.
- Advanced Control. You can modify almost every part of the login and registration experience. FusionAuth gives full flexibility to developers who want detailed customization.
- Standards and Integration. It supports WebAuthn and passkeys, enables multi-tenant architectures, and allows seamless user migration from legacy systems.
Auth0 Authentication and Identity Features
- Universal Login & SSO: Auth0 offers a hosted Universal Login that works across apps and enables single sign-on so a user logs in once and accesses multiple services.
- Multi Factor and Passwordless. Auth0 supports multiple authentication methods, including SMS, email, authenticator apps, and biometrics. It also allows passwordless login using magic links or one-time codes.
- Social and Enterprise Logins. It easily connects with major social providers such as Google, Apple, and Facebook , as well as enterprise identity solutions like Active Directory.
- Anomaly Detection. Auth0 constantly monitors how and where users log in. When it notices something that doesn't fit a user's normal pattern like access from a new device or location it reacts instantly.
- Standards and Integration. Auth0 supports modern authentication standards like WebAuthn and passkeys and can handle user migration from older systems with minimal effort.
Security & Compliance
Both FusionAuth and Auth0 focus on keeping data safe. When evaluating Fusionauth vs Auth0, their security and compliance features show how each platform protects data differently.
FusionAuth Security and Compliance
- Core Security Features. FusionAuth offers strong protection through login auditing and session management and password policy controls. It can detect impossible travel events like a user logging in from two distant locations in a short time.
- Advanced Protection. Higher plans include breached password detection that checks user credentials against known leaked databases and also add advanced threat detection and flexible MFA options.
- Control and Transparency. FusionAuth gives you complete visibility into your security setup. You decide how data is stored and monitored which is ideal for companies that prefer full control over their compliance process.
- Regulatory Advantage. FusionAuth’s ability to host in-region or on-premises gives companies in regulated industries a strong compliance edge. It helps them keep data within their own control and meet privacy and legal rules without relying on outside cloud systems.
Auth0 Security and Compliance
- Built-in Protection. Auth0 provides enterprise-grade security even in its basic plans. It includes built-in features like bot detection, anomaly detection, and breached password scanning.
- Certifications and Compliance. Auth0 meets strict global standards with SOC 2 Type II certification and GDPR compliance.
- Automatic Maintenance. Since Auth0 runs fully on the cloud it handles all patches and security updates automatically. This reduces workload for teams and ensures that your system always stays protected with the latest safeguards.
Deployment & Hosting Flexibility
FusionAuth and Auth0 differ in how they handle deployment and hosting. One offers full control while the other simplifies management.
FusionAuth - Deployment and Hosting Flexibility
- Hosting Options. FusionAuth can run anywhere you choose, including your own servers or major cloud platforms like AWS, Azure , and Google Cloud. It also supports on-premises deployments for organizations that need complete data control or must meet compliance requirements.
- Deployment Control. You decide how and when to update or scale your system. It gives you full control over uptime and performance.
- Cost Management. Self-hosting keeps your costs predictable. There are no per-user fees that grow as your user base increases.
- Data Ownership. Your data always stays with you which makes it ideal for industries that require strict data privacy or region-based storage.
Auth0 - Deployment and Hosting Flexibility
- Cloud-Based Platform. Auth0 runs in the cloud on Okta's global infrastructure. You don't manage servers or updates. Everything is handled for you.
- Simple Deployment. Setup is quick and requires no DevOps work. The platform automatically manages scaling security patches and uptime.
- Private Cloud Option. Enterprise users can choose private cloud deployment for more control while still getting a managed experience.
- Limited Customization. You cannot self-host Auth0 or choose your own cloud regions. Infrastructure control stays with Auth0.
Developer Experience & Ecosystem
Developers work best with tools that are simple and flexible. The FusionAuth vs Auth0 developer experience shows how each platform balances customization and simplicity.
FusionAuth Developer Experience
- Documentation and APIs. FusionAuth has clear documentation that developers find helpful. Its APIs are simple and well explained with examples for quick setup.
- SDK Support. It provides SDKs for multiple programming languages, including JavaScript , Python, Java, .NET, and PHP, making integration simple and efficient.
- Customization. You can change workflows as you want. Webhooks and APIs help you add extra functions when needed.
- Self Hosting. Since FusionAuth can run on your own servers you can see everything directly and fix issues fast.
- Community Support. Developers can get help through forums, GitHub , and Slack, where the community is active, helpful, and responsive.
Auth0 Developer Experience
- Easy Setup. Auth0 gives quick start guides and simple steps for all major frameworks. The dashboard helps you set things visually without much code.
- SDK Coverage. Auth0 supports a wide range of development tools, including React, Angular, Vue, Node.js, .NET, and Ruby. All SDKs are regularly updated and maintained for reliability.
- Extensions and Integrations. The marketplace includes ready tools for passwordless login and social logins and other common use cases. Integration with developer tools is simple.
- Support. Auth0 offers community help on free plans and faster ticket or phone support on higher plans.
Pricing & Support
FusionAuth Support and Pricing:
FusionAuth provides flexible deployment options with transparent pricing. You can self-host for free or choose managed hosting with professional support.
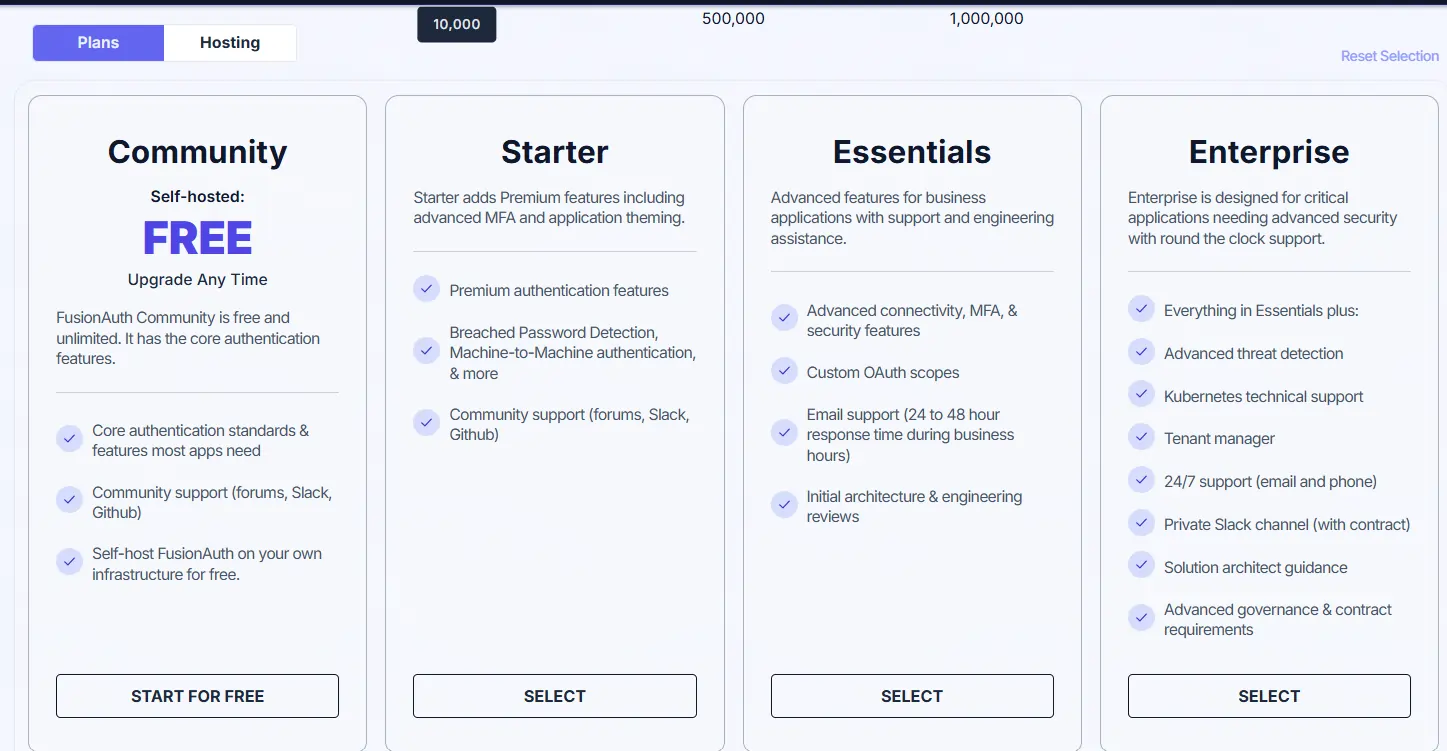
FusionAuth Pricing structure:
- Community plan: Free (self-hosted, unlimited users)
- Starter plan: Starts at $125/month (up to 10,000 MAUs)
- Essentials plan: Around $850/month (up to 10,000 MAUs.)
- Enterprise plan: $3,300/month (10,000 MAUs)
- Pricing remains stable — no extra charges as user count grows
Auth0 Support and Pricing:
Auth0 offers a cloud-managed identity solution with scalable pricing based on Monthly Active Users (MAUs). Plans include flexible support options for growing teams.
Auth0 Pricing Structure:
- Free plan: Up to 25,000 MAUs, includes custom domain and social logins.
- Essentials plan: $35/month, up to 500 MAUs with MFA and RBAC.
- Professional plan: $240/month, up to 1,000 MAUs with advanced MFA and custom databases.
- Enterprise plan: Custom pricing with 99.99% SLA, unlimited orgs, and dedicated support.

Use Cases of FusionAuth and Auth0
Every product needs a secure and simple way for users to log in. FusionAuth and Auth0 both help you do that but in their own unique ways. The best choice depends on what matters most to your team whether it is full control or an easy setup that just works.
When FusionAuth Makes Sense
- Built to Scale. If you are building a product that will grow fast FusionAuth keeps costs steady even as your users increase.
- Private Hosting. It fits well for industries like healthcare and finance and government where data must stay in a private environment.
- Complete Customization. Good for teams that want full control over how login pages and authentication flows look and work.
- Hands On Teams. Works best for teams that can manage servers and handle setup and maintenance on their own.
When Auth0 Makes Sense
- Quick Launch. If you need authentication ready fast Auth0 helps you go live in a short time.
- Managed Service. Great for teams that want to focus on their product while Auth0 takes care of security and hosting.
- Social Logins.Perfect for users who prefer signing in with Google , Apple, Facebook, or Microsoft, without requiring any additional setup.
- Small or Mid Projects. Works well when your user base is small or growing slowly since pricing stays reasonable.
- Strong Support. Helpful for teams that need reliable help and fast responses when issues appear.
Limitations and Challenges of Auth0 vs FusionAuth
FusionAuth and Auth0 both offer great solutions but they come with their own challenges.
FusionAuth - Limitations and Challenges
- Technical Management. Running FusionAuth yourself means you need people who can handle setup and server maintenance. It gives control but also adds more responsibility.
- Missing Advanced Features. The free version covers the basics but for features like advanced MFA or enterprise tools you need a paid plan.
- Smaller Ecosystem. FusionAuth has fewer built-in integrations and a smaller community so sometimes you may have to create your own solutions.
- Limited Documentation. The guides are clear but not as deep as Auth0's. For tricky cases you might need to look through community forums or reach out to support.
Auth0 - Limitations and Challenges
- High Cost at Scale. Auth0 is easy to start with but as your user count grows the monthly cost increases quickly since it charges per active user.
- Less Customization. You work within Auth0's structure which limits how much you can change. Special authentication flows might need extra effort.
- Cloud Only. You cannot host Auth0 on your own servers which can be a problem for businesses that need strict data control or on-premises systems.
- Vendor Dependence. Since Auth0 is part of Okta now changes in pricing or direction could affect your setup in the future.
- Challenging Pricing. The tiered pricing and monthly active user model can be confusing making it harder to plan costs clearly.
- Difficult Migration: Moving users or leaving Auth0 is hard because user data and passwords are stored in a special way
Infisign: A Modern Alternative to FusionAuth and Auth0
Infisign keeps your business safe. Today, even one weak account can put everything at risk. Infisign makes sure that never happens. With UniFed, all your customer logins come together in one secure place. With IAM Suite, your team can log in without passwords. They can use biometrics and other secure methods that make work faster and safer.
Infisign uses advanced AI to monitor every login and block threats before they reach your systems. Every user is verified, every device is managed, and every action is tracked through a Zero Trust IAM framework.
With Infisign, security works quietly in the background so you can focus on growing your business. You can move forward with confidence, knowing your data, people, and systems are always protected.
Advanced Authentication & Access Control
- Universal Single Sign-On. Infisign takes only 4 hours to set up. You don't need long plans or outside help. Since there are no passwords, hackers have nothing to steal. The cloud-native system links your apps automatically, with no servers and no coding.
- Infisign's Smart Multi-Factor Authentication (MFA). Infisign uses adaptive MFA that learns from every login and changes security as needed in real time. It monitors each sign in and knows when something feels unsafe. When risk is high it asks for extra proof before letting the user in. It stops brute force attacks as soon as they start and blocks logins from unsafe places. It works with fingerprints, face scans, voice patterns, hardware tokens, push alerts and SMS codes to protect every account. Real users can sign in fast and fake users are stopped right away.
- App Integration Platform. The Infisign App Integration Platform connects 6000+ apps across your systems. Even older software becomes more secure and powerful, without any coding. Full integration is ready in hours instead of months.
- Conditional Access Policies. Infisign uses conditional access to decide who can sign in and when. It looks at simple things like the user role, the device being used and the location of the login. If everything looks normal access is allowed right away. If something feels unusual the system asks for extra proof or blocks the login. This way only trusted users get in and your data stays safe without making the process slow or difficult.
- Automated User Management. Automated User Management gives new employees the access they need instantly. When someone leaves their access is removed in thirty seconds. This keeps your system secure and your team ready to work right away.
- AI Access Assistant. AI Access Assistant takes care of access requests, so IT teams don't get overwhelmed. Employees can get approvals right away through Slack or Teams. The AI learns from daily work patterns and makes the process smarter over time. It also spots and stops suspicious actions before they cause any damage.
- Privileged Access Management. Infisign’s Privileged Access Management keeps admin accounts safe with Infisign’s Zero Trust design. It checks every important action to be sure the person doing it is real and has the right permission. All admin activity is monitored all the time to keep your system secure. Infisign also uses Just in Time access so admin rights appear only when someone needs them and go away as soon as the work is done. Third-party vendors get just-in-time access that ends when their work is done so the main network stays protected.
- Compliance and Auditing. Infisign’s IAM compliance system automatically records every login and user action. Reports for GDPR, HIPAA , and SOX are generated instantly without any manual effort. Compliance teams can access user activity at any time, and complete audit logs remain available for verification whenever needed.
- Identity Governance and Administration (IGA) helps companies control who can access what inside their systems. It makes sure every user has only the access they need and nothing more. It also keeps full records of every change to meet security and compliance rules.
- Non-Human Identity. Non-Human Identity covers every account that is not a person. In every business systems are used by bots, APIs, and service accounts. These accounts do important work but if they are not managed they can create security risks. Infisign protects them by removing passwords and applying clear access rules. This keeps automation safe, stops hackers and ensures that all systems run smoothly.
- Network Access Governance( NAG). Infisign’s Network Access Gateway brings Zero Trust security to on-premise and hybrid systems. Remote users connect to internal servers through encrypted TLS tunnels that keep data safe during transfer.
- Role-based access control decides who can reach each system and who cannot.
Additional Core Features
- Zero-Knowledge Authentication. Zero Knowledge Authentication lets you prove your identity without sharing your secret information. Passwords and credentials stay only on your device and never leave it. The server cannot see or store them in any form. Even if the server is hacked the data on your device stays safe. This method protects both users and machines. Employees bots and APIs can sign in safely and businesses get strong security without extra work or high cost.
- Passwordless Authentication System. Infisign's Passwordless Authentication removes the need for traditional passwords. You can log in with your fingerprint or face. Biometrics are unique to you so no one else can copy them. One time codes can go to your trusted devices or magic links can give instant access. The system connects your login to all business tools so you can move between email collaboration software and other apps safely and easily.
- MPWA and Password Vault Feature. Infisign's MPWA makes your old software work safely with new login systems. Infisign MPWA connects older apps to modern authentication without any risk. Managed Password Web Authentication handles all passwords automatically and keeps them in a secure vault. You never need to remember or type them again and your logins stay safe at all times.
Deployment Architecture
Deployment Architecture uses a cloud native design that sets up quickly without extra hardware. Your business can start small and scale into a full enterprise system with ease. Updates happen automatically so everything stays secure and stable. Infisign supports deployment in cloud, on-premise, and hybrid environments so you can choose what fits your infrastructure now and adapt later.
The Real Difference
FusionAuth gives control but needs infrastructure management. Meanwhile, Auth0 offers convenience but adds cost per user and limits flexibility. Infisign gives both control and ease with enterprise features: simple deployment predictable costs and silent security that runs in the background.
You no longer need to pick between control and convenience. Infisign gives you both. You get real protection that fits the way modern businesses work.
Security stays strong and your team stays fast. Authentication runs quietly in the background so you can focus on what matters most — growing your business.
Try Infisign now and experience secure access that just works.
FAQs
What is FusionAuth used for?
FusionAuth helps developers add secure login and user management to their applications. It supports single sign-on and API security while giving teams complete control over their setup. Its pricing remains consistent regardless of the number of users, making it a flexible and cost-effective choice.
What are alternatives to Auth0?
Auth0 alternatives include Infisign for AI based adaptive security, FusionAuth for self hosting, Okta for enterprise identity, Amazon Cognito for AWS users, and Azure AD B2C for Microsoft environments.
What are alternatives to FusionAuth?
Infisign is the best alternative, offering fast setup and intelligent AI-driven security without the need to manage any infrastructure. Other notable options include Auth0 for managed cloud solutions, Keycloak for open-source control, Okta for enterprise identity management, and AWS Cognito for applications built on AWS platforms.
Are Okta and Auth0 the same thing?
Okta acquired Auth0 in 2021 yet both continue to function as separate platforms with distinct features, pricing and market focus. They now share technology and vision but still serve different identity needs.
Is Auth0 SAML or OIDC?
Auth0 works with both SAML and OIDC along with OAuth 2.0. It gives you the freedom to choose what suits your app best. Companies often use SAML for internal tools while developers building modern web or mobile apps usually go with OIDC. Auth0 makes both options easy to set up and manage without needing deep security knowledge.




























