Ticketmaster lost 560 million records. AT&T exposed 70 million accounts. Change Healthcare breached 100 million individuals. The pattern stays the same - manual user access management creates deadly gaps.
Ex-employees keep system access for weeks. New hires wait days for permissions. The average breach costs $4.88 million. Nearly 78% of companies disclosed identity-related breaches.
User lifecycle management software eliminates these manual gaps. It automates user provisioning from hire to retire. Modern systems prevent the identity vulnerabilities that cause most breaches.
Best User Lifecycle Management Software: A Detailed Comparison
What Is User Lifecycle Management (ULM) Software?
User Lifecycle Management Software is a system that manages user access throughout their entire journey in your organization. It handles every step from hiring to firing automatically.
The software automates three key stages for you.
- Creates accounts for new hires instantly.
- Updates access when people change roles.
- Removes access when employees leave your company.
This system connects with your HR database directly. When HR adds someone new, accounts get created automatically. When someone quits, access gets removed right away. No manual work needed from your IT team.
Here are the four main parts every good system includes.
- Identity Creation and Provisioning. The system creates new user accounts automatically. It gives each person the right access for their job. No more manual account setup or guessing what access someone needs.
- Access Management. The system updates permissions when roles change. Employee gets promoted? Access updates instantly. Someone switches departments? New permissions apply right away.
- Monitoring and Compliance. The system tracks what users do every day. It spots unusual behavior that might signal security problems. It keeps detailed logs for audit reports too.
- Deprovisioning and Offboarding. The system removes access when employees leave. It happens fast to keep your data safe. No more worrying about ex-employees accessing company files.
These four parts work together to create a complete security system. They protect your company while making IT work easier. Each part handles a different stage of the employee journey. Together, they keep your business running smooth and secure.
10+ Top User Lifecycle Management Software (2026 Edition)
1. Infisign ULM
Infisign is one of the best user lifecycle management software. It has AI access assist built inside. It also has automatic provisioning and deprovisioning features. The system works on a zero-trust framework. This makes assigning access to applications quick and easy. Security breaches become less likely than with other ULM software.
Key Features:
- AI-Powered Access Intelligence. Smart AI watches user behavior patterns 24/7. It spots unusual access requests that signal threats. The system learns your company's normal patterns and flags anything suspicious. This catches insider threats before they cause damage.
- Zero Trust Architecture. Every access request gets verified regardless of source. Authenticate all system interactions through robust identity management and incorporate zero-trust principles that verify every access request regardless of source. No user gets trusted by default, eliminating 75% of common attack vectors.
- Passwordless Authentication. Eliminates the biggest security weakness in most companies. Perhaps one of the most significant challenges cybersecurity organizations face is concerning unauthorized access through stolen passwords. Users authenticate through biometrics or device-based keys. This stops 80% of breaches instantly.
- Automated Lifecycle Management. Connects with your HR systems to handle user onboarding and offboarding processes instantly. New hire gets added to HR? Access gets created in 30 seconds. Employee quits? All access gets revoked in 10 seconds.
- Real-Time Risk Intelligence. Monitors every access request for risk factors like unusual location, device, or time. AI and machine learning become integral to identity verification systems providing instant threat detection. High-risk requests get blocked automatically.
- 6000+ App Integrations. Comprehensive integration library supports major enterprise applications and cloud services. Pre-built connectors eliminate custom development requirements for most business systems. Legacy applications connect through standardized protocols seamlessly.
- Adaptive MFA. Context-aware multi-factor authentication adjusts security requirements based on risk assessment. Low-risk scenarios streamline user experience while maintaining security standards. High-risk situations enforce additional verification layers appropriately.
- The AI Access Assist automates access approvals. It also lets you quickly approve or deny requests using Slack and MS Teams
- Compliance Support. Built-in compliance frameworks address regulatory requirements across multiple industries automatically. Comprehensive audit trails track all user activities for regulatory reporting. Documentation generation supports various compliance standards including SOX, GDPR and HIPAA.
- Single Sign-On (SSO). Infisign’s SSO eliminates password sharing while providing seamless application access. Users authenticate once to access all authorized enterprise applications securely. Integration supports SAML, OIDC, and OAuth protocols comprehensively.
- Advanced Access Control. Granular permission management enables precise resource access control throughout the organization. Role-based access control ensures users receive appropriate privileges only. Dynamic permission adjustment responds to changing organizational requirements automatically.
- Deployment Flexibility. Multi-environment support accommodates cloud, hybrid, and on-premises infrastructure configurations. The platform adapts to existing organizational technology stacks without requiring infrastructure changes. Deployment options support various enterprise architectural requirements effectively.
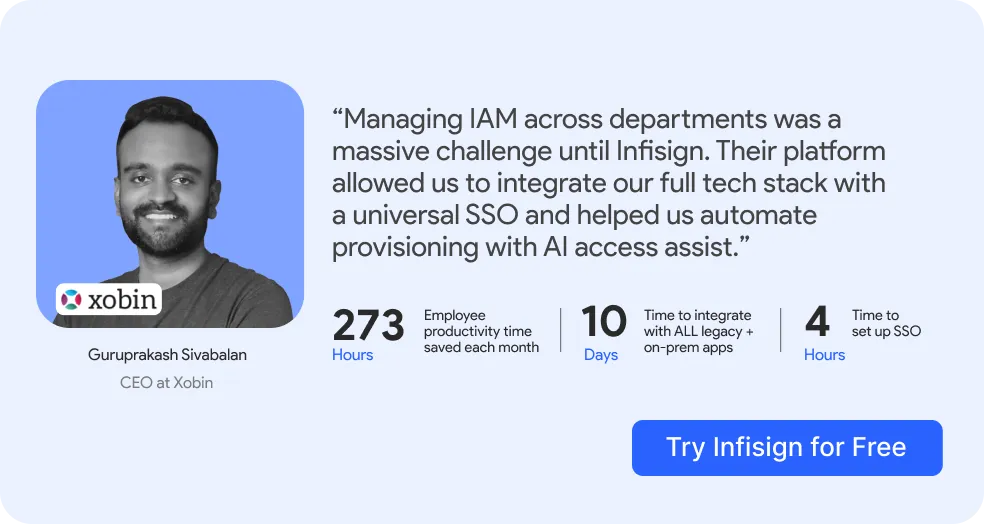
How Infisign Unified Multiple IdPs for a Global Manufacturing Giant
Infisign acts as a central identity gateway for one of our MAJOR manufacturing clients’ fragmented identity landscape. We removed productivity bottlenecks, security risks, and EXPENSIVE delays.
Infisign unifies the entire ecosystem, bridging disparate directories and tools without replacing costly legacy infrastructure.
How Infisign Helped Our Leading Manufacturing Client:
- Shattered Identity Silos: Created a single source of truth by syncing with all existing IdPs (like Azure AD, Cognito), instantly bridging disparate systems.
- Universal Single Sign-On (SSO) Experience: Delivered a true Single Sign-On experience, authenticating users once for secure, immediate access to every application they need.
- Effortless Legacy App Access: Wrapped decades-old, on-premise applications in a zero-trust security framework, removing vulnerabilities without rewriting a single line of code.

Pros:
- AI learns your specific threat patterns
- Zero passwords eliminate biggest attack vector
- Works with any existing system or app
- Saves 60% on identity management costs
- Real-time threat detection built-in
Cons:
- Passwordless authentication requires the use of its encrypted password vault feature.
2. Microsoft Entra ID
Microsoft Entra ID works best for Microsoft-heavy environments. Formerly Azure Active Directory, it handles user provisioning and lifecycle management across Office 365 and Azure clouds. Perfect for companies already invested in the Microsoft ecosystem.

Key Features:
- HR-Driven Provisioning. The system provisions or deprovisions user access. It gets signals from HR systems like Workday. It also works with SAP SuccessFactors, Microsoft Dynamics 365, and Aquera.
- Template-Based Automation. You can use templates to automate common tasks. The system automates identity and access tasks for user changes. It handles the first day for new users.
- Cloud App Integration. The platform provides seamless integration with thousands of cloud applications. Your team gets easy access to all tools.
- Conditional Access. The system provides advanced risk-based access policies. It keeps your data safe from threats.
Pros:
- Deep integration with Microsoft products
- Strong template library for common scenarios
- Thousands of pre-built app connections
- Enterprise-grade security features
Cons:
- Works best only with Microsoft ecosystem
- Complex pricing that scales with features
- Can be overwhelming for non-Microsoft shops
3. IBM Verify
IBM Verify provides both IAM and CIAM software capabilities in one platform. Built for enterprise user lifecycle management across complex hybrid environments. Handles both employee access (IAM) and customer access (CIAM) from a single console.

Key Features:
- Hybrid Environment Support. The system optimizes for complex IT environments. It spans on-premises, cloud, and hybrid infrastructures.
- Advanced Risk Assessment. AI-powered risk analysis provides adaptive authentication. The system learns from user behavior patterns.
- Enterprise Integration. Deep integration works with IBM's broader enterprise software suite. Your existing tools connect easily.
- Multi-Factor Authentication. Comprehensive MFA options include biometric authentication. Users get multiple security layers.
Pros:
- Handles both employee and customer identities
- Strong support for hybrid cloud environments
- Advanced AI-powered risk assessment
- Enterprise-grade scalability and features
Cons:
- High cost makes it expensive for smaller companies
- Complex setup requires IBM expertise
- Overkill for simple single-cloud environments
4. SailPoint IdentityNow
SailPoint IdentityNow SailPoint focuses on identity governance for large enterprises. The user lifecycle management software platform uses AI to manage user identities throughout their complete lifecycle. Strong choice for companies needing advanced compliance and governance features.

Key Features:
- AI-Driven Governance. Sailpoint uses AI and machine learning together. This speeds up identification and management of risks. The system allows automated provisioning, access certifications, and audit reporting.
- Automated Access Control. The system automates user access across many systems. It works with applications based on role changes.
- Access Governance. The platform grants, reviews, and certifies user access rights. It bases decisions on policies to ensure compliance.
- Zero Trust Framework. This identity lifecycle management software supports zero-trust security. It allows businesses to stay compliant.
Pros:
- Industry-leading AI governance capabilities
- Comprehensive access control automation
- Excellent compliance and audit tools
- Strong zero trust security implementation
Cons:
- Very expensive for small to medium businesses
- Long implementation timeline (6+ months)
- Complex interface requires training
5. Okta Lifecycle Management
Okta Lifecycle Management makes user access easier. It works across a range of applications. The system reduces complexities of managing user identities. This happens in modern environments. Okta has a comprehensive identity platform. It serves businesses of all sizes.

Key Features:
- Automated JML Process. The system helps with employee lifecycle management. It automates account provisioning, role adjustments, and deactivation.
- Flexible Access Control. The platform supports granular permissions for employees. It also works for contractors and external users. Access gets given and rescinded based on role.
- Universal Directory. The system provides a single source of truth. It handles all user identities and attributes.
- Extensive App Catalog. Okta offers an Okta integration network (OIN). This is an application network. It includes built-in features like provisioning and active directory (AD).
Pros:
- Largest application catalog in the industry (7000+ apps)
- Flexible access controls for any user type
- Strong universal directory capabilities
- Good for companies of all sizes
Cons:
- Gets expensive quickly with many users
- Some applications require additional setup work
- Advanced governance features cost extra
6. OneLogin
OneLogin lets employees and administrators manage identities through their user lifecycle management software system. The platform works with on-premises and cloud directories. This creates an identity management experience. It works across multiple platforms and applications

Key Features:
- SmartFactor Authentication. The platform's machine learning-powered SmartFactor Authentication works smart. It adjusts access controls based on risk levels. This ensures sensitive data gets protected. It does this without compromising usability.
- User Provisioning. The system automates granting and revoking user access. It works with applications to allow proper access rights. This reduces administrative overhead.
- Cloud Directory. The platform manages identities across cloud and on-premises environments. It works with existing infrastructure.
- Risk-Based Authentication. The system uses machine learning to assess access risks. It adjusts security requirements based on data. This balances usability with security.
Pros:
- Intelligent risk-based authentication system
- Good support for hybrid cloud/on-premises environments
- User-friendly interface and setup process
- Strong machine learning capabilities
Cons:
- Smaller app integration library than competitors
- Can be slow with very large user populations
- Advanced features require higher-tier plans
7. Ping Identity
Ping Identity is a solution in enterprise user lifecycle management. It has tools to manage user identities. These tools work across various stages. With Ping, businesses get secure onboarding. They also get offboarding. This provides experience for administrators and users.

Key Features:
- Identity Provisioning. The system assigns roles and permissions. It bases decisions on user attributes. This ensures compliance and access control across all systems.
- Access Requests. The platform simplifies users requesting more access. This reduces helpdesk costs while maintaining control. Permissions stay managed properly.
- Advanced SSO and MFA. The platform has advanced features like Single Sign-On (SSO). It also has Multi-Factor Authentication (MFA). These add security throughout the lifecycle.
- API Security. The system has a strong focus on securing APIs. It also secures microservices.
Pros:
- Excellent API security and developer tools
- Advanced SSO and MFA capabilities
- Good choice for modern application architectures
- Flexible identity provisioning system
Cons:
- Complex setup for non-technical users
- Higher cost than simpler alternatives
- May be overkill for basic identity needs
8. JumpCloud
JumpCloud provides unified identity and device management in a single cloud platform. Eliminates the need for separate identity and device management tools. Perfect choice for companies managing diverse operating systems and remote teams.

Key Features:
- Unified Platform. The system combines identity and device management. Everything works in a single solution.
- Cross-Platform Support. The platform works across Windows, Mac, and Linux environments. All your systems connect together.
- Automated Access Control. Dynamic group-based access provisioning works. Users get the right access at the right time.
- Cloud-Native Architecture. No on-premises infrastructure gets needed. Everything runs in the cloud.
Pros:
- Combines identity and device management
- Works on all major operating systems
- Pure cloud solution with no on-premises requirements
- Excellent for remote and distributed teams
Cons:
- Fewer enterprise governance features than specialized tools
- Limited advanced compliance capabilities
- May not scale for very large organizations
9. Rippling
Rippling combines HR and IT functions in a single user lifecycle management software platform. Handles employee management from hiring through IT provisioning to offboarding. Best choice for growing companies wanting unified HR and IT operations.

Key Features:
- Automatic Provisioning. The system provisions users in software. It also works with devices and IT systems. This happens during onboarding.
- Offboarding Automation. The platform removes access to all company systems. This happens when an employee leaves.
- HR Integration. The system syncs with HR systems. This enables smooth employee data updates.
- Comprehensive IT Management. Beyond identity management, it includes device management. It also includes application management.
Pros:
- All-in-one HR and IT solution saves time
- Strong automation reduces manual work
- Good choice for fast-growing companies
- Seamless employee data management
Cons:
- May be too broad for companies wanting specialized IAM
- Less specialized than pure identity management tools
- Complex initial setup with many integrations
10. Saviynt
Saviynt offers cloud-native user lifecycle management tools with advanced identity governance capabilities. Built specifically for cloud environments with strong analytics and risk intelligence features.

Key Features:
- Cloud-Native Architecture. The system gets built for cloud environments. Everything works in the cloud.
- Advanced Analytics. AI-powered insights help with access governance. You get smart recommendations.
- Risk Intelligence. Comprehensive risk assessment and mitigation work together. Your security stays strong.
- Privileged Access Management. Integrated PAM capabilities come built inside. High-level access gets managed properly.
Pros:
- Modern cloud-native design and architecture
- Strong analytics and AI-powered features
- Built-in privileged access management
- Good risk intelligence capabilities
Cons:
- Newer company with less market presence
- Can be complex for organizations with simple needs
- Higher learning curve than basic solutions
11. MiniOrange
MiniOrange focuses on real-time synchronization across user lifecycle management platform environments. Specializes in bidirectional data flow between different directory systems and applications.
Key Features:
- Real-Time Synchronization. Instant updates happen across all connected systems. No waiting time exists.
- Bidirectional Sync. The system ensures consistency across many directories. Data flows both ways in a perfect way.
- Broad Integration Support. The platform works with various HR systems. It also works with AD, LDAP, and cloud directories.
- Role-Based Security. MiniOrange enhances security by implementing role-based access control. It grants user access when necessary.
Pros:
- Excellent real-time synchronization capabilities
- True bidirectional data flow between systems
- Wide range of integration options
- Affordable pricing for most organizations
Cons:
- Less advanced governance features than enterprise tools
- May lack sophisticated compliance capabilities
- Limited reporting and analytics features
Why User Lifecycle Management Software Is Critical for IAM Success
User access lifecycle management is critical because manual identity management creates dangerous security gaps. Most companies still use old tools like Active Directory. These tools fail when you need to add many users quickly. They make mistakes with user data and create messy logs.
Your organization needs automated provisioning through user lifecycle management software to stay secure and efficient. Manual processes put your business at risk every single day. Smart companies choose automation to protect their valuable data.
Here are the five main benefits every business gets from proper implementation.
- Enhanced Security Posture.The software removes access instantly when employees leave. This prevents unauthorized access to sensitive systems and data. Automated processes eliminate human delays that create security gaps.
- Operational Efficiency. Your IT team gains time for strategic innovation projects. Automated workflows handle routine provisioning tasks instantly. The user lifecycle management platform transforms IT from reactive support to proactive business enablement.
- Compliance and Governance. Role-based controls enforce policies automatically. Automated tracking creates complete audit trails showing who accessed what and when. These detailed logs help auditors verify compliance quickly and reduce audit preparation time significantly.
- Improved User Experience. New employees get access to tools on day one. They start working immediately without waiting for IT setup. Happy workers stay productive and satisfied with your company.
- Cost Management. You stop paying for unused software licenses. Regular audits show exactly who uses what applications. Smart tracking prevents wasteful spending on inactive accounts.
These five benefits work together to eliminate manual security gaps. Each benefit strengthens the others. Better security enables efficiency. Efficient processes improve compliance. Strong compliance builds user trust. User lifecycle management tools become essential for complete organizational protection.
How to Choose the Right User Lifecycle Management Tool?
Selecting the optimal user lifecycle management tools requires careful evaluation of many factors. These factors align with your organization's specific needs and constraints. You must assess your current infrastructure first. Consider your unique business needs. Look at your growth plans and budget limits.
Here are six key factors you must evaluate when choosing your ULM tool.
- Assess Your Current Infrastructure. Begin by auditing your existing IT environment. Consider whether you operate in cloud, on-premises, or hybrid models. Look at your company's growth rate. Some ULM software face timeouts when scaling users.
- Evaluate Integration Needs. List your current applications and systems first. Some solutions work better with specific technology stacks. Others offer broader third-party support. Choose based on your existing infrastructure and future integration plans.
- Consider Scalability and Performance. Plan for growth, not just current needs. Automated onboarding and offboarding become critical as you scale. More than 1,800 data breaches occurred in 2022 often because manual processes break under pressure. Your ULM must handle 10x growth.
- Security and Compliance Needs. Different industries have varying compliance needs. ULM audit trails track every user interaction. Detailed logs help monitor user behavior. This maintains regulatory compliance.
- Budget and ROI Considerations. Factor in initial licensing costs. Include implementation, training, and maintenance expenses. Consider cost savings from reduced manual processes. Improved security saves money long-term.
- User Experience and Adoption. The best ULM solution is one users embrace. Look for intuitive interfaces and smooth experiences. A centralized management point simplifies user access oversight.
These six factors work together for optimal ULM selection. They ensure your solution meets current needs and supports future growth. Each factor influences the others to create maximum value. Evaluate all factors together for the best decision.
When Should You Invest in User Lifecycle Management Software?
Organizations should think about using user lifecycle management software when they see these warning signs. These signs show your current manual work cannot handle your business needs. Smart companies act on these signals before problems become costly disasters.
Here are five warning signs that demand immediate action:
- Fast Growth Creates Security Gaps. Your company hires more people but IT processes stay manual. New employees wait days for system access. Departing employees keep access for weeks after leaving. This creates security risks during busy growth periods.
- Security Incidents Force Action. One breach changes everything fast. Companies realize manual access control creates vulnerabilities. Regulatory audits expose gaps in user management. Leadership demands automated solutions immediately.
- Multiple Applications Create Complexity. Employees need access to dozens of different systems daily. Manual provisioning becomes impossible to manage properly. IT teams lose track of who has access to what. This creates compliance problems and security holes.
- Remote Work Increases Risks. Distributed teams make access management much harder. Home networks and personal devices expand attack surfaces. Manual processes cannot secure remote access properly. Automated controls become essential for remote security.
- Manual Processes Waste Money. Slow access removal costs thousands in unused licenses monthly. Delayed onboarding reduces new employee productivity significantly. Manual provisioning requires expensive IT staff time. Automation pays for itself through these savings.
Smarter User Lifecycle with Infisign
Traditional IAMs systems created the problem they claim to solve. 90% of organizations had at least one identity-related attack in 2023. Why? Because centralized password databases become single points of failure that attackers target first.
- No Central Database System. No central database means no single failure point. 99% of cloud breaches happen from configuration errors. Infisign removes configuration errors that cause breaches.
- AI-Powered Access Intelligence. Smart AI learns your normal patterns. It flags threats instantly. AI systems watch user behavior to spot unusual login patterns. This catches insider threats before damage happens.
- Passwordless Authentication System. Infisign pioneered the first Identity and Access Management platform that eliminates passwords completely. Trusted digital identity gets created on user devices. Traditional passwords create major security risks. Passkeys using modern standards are gaining popularity.
- Complete Lifecycle Automation Process. Automated provisioning and role updates happen instantly. User lifecycle management platform features include real-time HR integration. New hires get access in 30 seconds. Departing employees lose access in 10 seconds.
- Zero Trust Security Framework. Every access request gets verified regardless of source location. Zero trust security constantly verifies users at set intervals. This monitors for suspicious activity based on device health.
- Cost Optimization Benefits. Reduces identity management costs by 60% while improving security. Strong security strategies need measurable outcomes. This includes improved efficiency and reduced costs.
The future of user lifecycle management requires intelligent automation and zero-trust security. Infisign delivers both while eliminating the password vulnerability that causes 90% of breaches.
Ready to eliminate your identity security risks?
Schedule your free demo today and see why leading enterprises choose Infisign for user lifecycle management software.
FAQs
What is user lifecycle management?
User Lifecycle Management is a systematic approach to managing user identities and access rights throughout their entire organizational journey. It automates identity creation, access provisioning, and account deactivation based on employee roles. The process handles onboarding, role changes, security monitoring, and offboarding efficiently using specialized user lifecycle management tools.
What features should a user lifecycle management software have?
A good user lifecycle management software should include several key features to manage the complete user lifecycle.




























