You watch companies get hit by data breaches. Their stock prices crash overnight. This
Your employees wait hours for system access. New hires sit idle on day one. Former employees still access your systems. Current workers collect dangerous permissions over time.
Hackers target these weak spots. Compliance auditors demand instant proof. You scramble through scattered data for hours.
You need identity governance that thinks ahead.
IGA solutions turn security into competitive advantage. You protect data while enabling growth.
Best IGA Solutions Compared
What Are Identity Governance and Administration (IGA) Solutions?
Identity governance solutions are software tools that control access to company systems. They handle user accounts, enforce security rules, and maintain compliance records. These tools protect companies from hackers while making IT work easier.
Below are the main features that make IGA solutions essential for modern businesses.
- Managing User Accounts. Automatically create accounts when employees join and remove access when they leave—no manual work needed.
- Controlling Access. Ensure the right people get access to the right tools. For example, sales teams get access to sales platforms only.
- Setting Rules. Define who can access what. IGA blocks unauthorized users automatically. Finance workers see financial reports only. Marketing teams cannot view customer passwords. Each department gets proper access levels.
- Keeping Records. You get all activity logs saved automatically. Compliance reports generate instantly. Auditors get instant proof of access controls.
Why IGA Solutions Matter for Enterprises in 2026
Companies need IGA solutions more than ever in 2026. New security threats, strict laws, and remote work create big challenges. Digital changes and cloud systems make identity and access management complex. Modern businesses require robust iam solutions to maintain competitive advantage.
Here are the key reasons why businesses must use IGA solutions to stay safe and competitive.
- Insider Threat Prevention. Your employees pose the biggest security risk to your business today. IGA solutions automatically detect suspicious behavior and block unauthorized access before damage happens.
- Compliance Automation. You face strict regulations like GDPR and SOX that demand proof of access control. Advanced IGA framework implementations create automated audit trails, saving you from compliance headaches.
- Access Creep Control. Your workers collect permissions over time, creating security holes everywhere. Identity governance solutions enforce least-privilege access, removing unnecessary permissions that put your data at risk.
- Multi-Cloud Identity Management. You use multiple cloud platforms that create identity chaos across your organization. IGA solutions give you single-point control over all cloud environments and applications.
- Zero Trust Implementation. Hackers bypass your traditional security by targeting identity systems directly. Modern ABAC access controls enable continuous verification, ensuring only verified users access your critical business systems.
Top 11 Identity Governance and Administration (IGA) Solutions in 2026
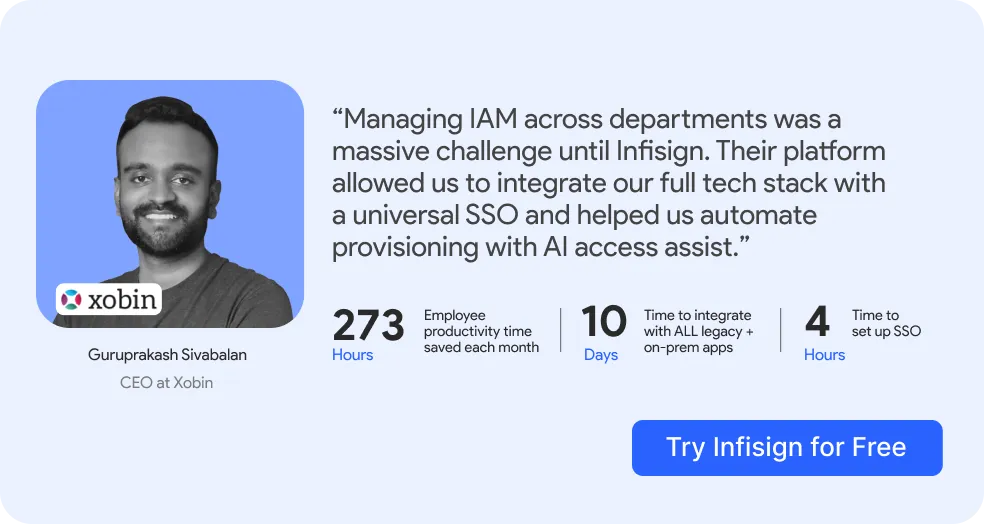
1. Infisign
Your business needs automated user lifecycle management today. You want complete control over who accesses what.
When it comes to security and complete visibility, Infisign stands out as the best identity and access management software on this list. With Infisign, your IT team gains centralized control across the board. Manage all permissions from a single dashboard. Enforce access policies across your entire infrastructure. And integrate with all systems—without disruption.
What makes this unique is the fact that it comes with conditional access, which ensures you don’t compromise on user experience. This is especially helpful for healthcare, fintech, and software companies, where data compliance laws like GDPR, HIPAA, and CCPA are essential.
Key Features:
- Adaptive MFA Security. Risk-based authentication adjusts based on user behavior. High-risk logins require additional verification steps. Low-risk access flows without friction.
- Machine Identity Security. You manage service accounts, bots, and automated processes securely. Non-human identities get proper access controls. System-to-system authentication becomes bulletproof.
- Automated User Lifecycle Management. Infisign provisions and deprovisions users across all applications automatically. New employees get correct access on day one. Departing staff lose access immediately.
- Centralized Access Governance. You control all user permissions from one dashboard. Role-based access controls ensure people get the right access levels. No more scattered permission management.
- Real-Time Compliance Monitoring. Infisign tracks all access activities and generates audit reports instantly. You meet regulatory requirements without manual work. Compliance becomes automatic.
- AI-Powered Risk Assessment. Smart algorithms detect unusual access patterns and security risks. You get alerts before breaches happen. Threats get blocked automatically.
- Policy-Driven Access Control. You set access rules once and they work everywhere. No finance person can approve their own expenses. No single person controls critical processes. Your business rules turn into automatic security.
- Cross-Platform Integration. Infisign works with over 6,000 apps, so you can easily connect your existing systems without having to replace anything. Whether you're using cloud, on-premise, or a hybrid setup, Infisign fits right in.
How Infisign Unified Multiple IdPs for a Global Manufacturing Giant
Infisign acts as a central identity gateway for one of our MAJOR manufacturing clients’ fragmented identity landscape. We removed productivity bottlenecks, security risks, and EXPENSIVE delays.
Infisign unifies the entire ecosystem, bridging disparate directories and tools without replacing costly legacy infrastructure.
How Infisign Helped Our Leading Manufacturing Client:
- Shattered Identity Silos: Created a single source of truth by syncing with all existing IdPs (like Azure AD, Cognito), instantly bridging disparate systems.
- Universal Single Sign-On (SSO) Experience: Delivered a true Single Sign-On experience, authenticating users once for secure, immediate access to every application they need.
- Effortless Legacy App Access: Wrapped decades-old, on-premise applications in a zero-trust security framework, removing vulnerabilities without rewriting a single line of code.

Pros:
- Zero-trust security framework protects against identity-based attacks instantly
- Automated governance reduces manual identity management work significantly
- Centralized dashboard gives complete visibility into all user access
- AI-powered risk detection prevents security breaches before they happen
Cons:
- Passwordless authentication requires password vault.
2. SailPoint Identity Security
SailPoint leads the IGA market through smart innovation and complete features. The company builds IAM solutions that help businesses control access.

Key Features:
- Machine Identity Security. Controls service accounts, bots, and RPAs. These non-human identities create security risks.
- Dynamic Access Roles. Changes user permissions based on job updates. Old static roles create security holes. Smart roles adapt when people change jobs.
- Universal Connectivity. Connects with existing company applications. Works with both old and new systems. No coding needed for most connections.
Pros:
- Unified dashboard system reduces training time and improves team collaboration across departments
- Regular feature updates throughout 2026 keep security capabilities current with emerging threats
- Advanced automation reduces manual governance tasks by 50% compared to traditional solutions
Cons:
- Premium pricing makes it expensive for smaller companies with limited IT budgets
- Complex feature set requires 3-6 months training investment for administrators to use effectively
- Implementation complexity increases with organization size and number of integrated applications
3. IBM Security Verify
IBM Security Verify uses IBM's long experience in business security. The platform works with Watson AI to make smart decisions. It helps companies manage user access across different systems.

Key Features:
- Watsonx.governance Integration. Manages AI agents across their entire lifecycle. Finds AI deployments that teams forgot about. Creates complete AI inventory for better control.
- Advanced AI Risk Detection. Watson AI finds suspicious user behavior patterns. Reduces manual review from days to minutes. Spots access problems before they become breaches.
- Login Security. Better security through robust mfa solutions and passwordless authentication methods. This reduces the need for traditional passwords.
Pros:
- Strong AI and machine learning through Watson integration with proven enterprise capabilities
- Great compliance and regulatory support with complete audit trails for regulated industries
- AI automation reduces manual governance work by 50% while improving accuracy
Cons:
- Hard learning curve and poor documentation for complex features requiring specialized expertise
- Too many false alerts in reporting systems creating extra work for teams.
- Complex implementation requires IBM expertise and extended training periods.
4. Okta
Okta IGA makes digital identity easy through its modern cloud approach. The platform focuses on automating identity work for businesses. Companies choose Okta for cloud-first IGA tools, making it ideal for modern identity governance needs.

Key Features:
- Smart Access Rules. Dynamic permission systems change access rights based on signals. Location matters for access decisions. Device security and multi-factor authentication affect permission levels. Protects company data without blocking real work.
- Cloud Design. Modern platform design removes old setup problems. It provides big, efficient iga tools. Updates happen without downtime or service breaks.
- Auto User Management. Complete automation of identity work processes. User setup happens fast across all applications. Reports work without manual effort from teams.
Pros:
- Easy interface with reliable platform and minimal downtime providing 99.9% uptime
- Strong automation capabilities eliminate repetitive manual tasks for IT administrators
- Cloud-native design provides better performance than legacy solutions
Cons:
- Extra costs required for migration, device keys, and directory sync features
- Basic identity tools that need improvement for many user roles and requirements
- Limited customization options compared to more flexible enterprise platforms
5. Microsoft Entra ID
Microsoft Entra ID gives complete identity tools for businesses. It works best with Microsoft systems like Teams and Azure. The platform creates a smooth experience for companies using Microsoft products.

Key Features:
- Access Control. Simple role-based access control gives people the right access. Special identity management handles temporary access to important resources. This keeps security strong while giving flexibility.
- Auto Workflows. Account setup happens without manual work steps. When people leave, their accounts get removed fast. This automation saves IT teams lots of time.
- Microsoft Connection. Works perfectly with Microsoft 365 and Azure services. All Microsoft platforms connect without problems.
Pros:
- Perfect for companies already using Microsoft products and existing infrastructure
- Cost-effective solution when bundled with existing Microsoft licensing agreements
- Extensive documentation and community support from Microsoft ecosystem
Cons:
- Limited options for companies using many non-Microsoft apps and third-party systems
- Complex features require careful planning to choose right options for implementation
- Advanced capabilities need Microsoft expertise and specialized training for administrators
6. One Identity Manager
One Identity Manager excels in providing comprehensive identity governance. The platform shows particular strength in SAP environments. Companies choose it for complex enterprise infrastructure needs.

Key Features:
- SAP Specialization Platform. Centralized management of SAP accounts with specialized workflows. Business logic and governance capabilities designed for SAP environments.
- Extensive Customization Framework. Flexible platform allowing creation of custom user interfaces. Teams get access based on application requirements.
- Privileged Access Integration. Seamless integration with privileged access management solutions. Provides granular control through different account types.
Pros:
- Exceptional SAP integration and specialization providing comprehensive governance for complex environments
- High degree of customization and flexibility enabling organizations to match specific requirements
- Strong privileged access management capabilities protect critical administrative accounts
- Mature platform with proven track record in complex enterprise environments
Cons:
- Complex implementation process requiring specialized expertise and significant planning for deployment
- Higher learning curve for administrators requiring extensive training and ongoing education
- Higher total cost of ownership due to customization and maintenance requirements
7. SAP Access Control
SAP Access Control handles identity management for SAP systems. The platform helps organizations control user access and meet compliance rules. It works with SAP environments to manage permissions and reduce security risks.
Key Features:
- Access Management. Controls user access across SAP systems completely. Manages user permissions and enforces company policies.
- Workflow Systems. Handles user account creation and updates smoothly. Manages role assignments based on job requirements.
- Risk Detection. Identifies security threats and access violations quickly. Uses data analysis to spot unusual user behavior.
Pros:
- Works with all SAP applications without extra setup or configuration requirements
- Provides detailed compliance reports for audits meeting regulatory industry standards
- Deep SAP expertise ensures compatibility with SAP updates and changes
Cons:
- Works only with SAP systems, no support for other enterprise applications
- Needs SAP experts to set up and manage requiring specialized knowledge
- Complex configuration process needs specialized SAP security expertise for implementation
8. Oracle Identity Governance
Oracle Identity Governance manages user accounts for large companies. The platform handles complex user access needs across different systems. It works with both cloud and on-site applications to control permissions.

Key Features:
- User Account Management. Creates and manages user accounts from start to finish. Controls what users can access in different applications.
- Smart System Design. Uses small software pieces that work together well. Finds patterns in how people use systems.
- Role Intelligence. Creates user roles without manual work using AI technology. Updates roles when job duties change over time.
Pros:
- Handles large companies with thousands of users well without performance issues
- Creates and manages user roles without manual work using advanced automation
- Comprehensive audit and compliance features meet regulatory requirements
Cons:
- Needs better web interface for easier daily use by administrators
- Costs a lot for licenses and ongoing support increasing ownership expenses
- Implementation complexity requires Oracle expertise and extended deployment timelines
9. Avatier Identity Manager
Avatier Identity Anywhere removes passwords from user login processes. The platform focuses on mobile access and user-friendly designs. It helps companies manage user accounts without complex password rules.

Key Features:
- No Password Login. Users access systems without typing passwords each time. People can request access and manage their accounts.
- Mobile Apps. iPhone and Android apps let users manage accounts. People can request system access during business hours.
- Security Options. Works with Duo, Google Authenticator, and Okta systems. Supports FIDO2 security keys for extra account protection. Integrates with existing security infrastructure easily.
Pros:
- Creates new user accounts with one button click automation
- Mobile apps make access requests quick and simple for users
- Compatible with current security infrastructure without extra expenses
Cons:
- Removing user accounts requires manual work steps from administrators
- Premium features need extra payments on top of basic subscription costs
- Complex installations need specialized consultants increasing project timelines
10. Omada Identity
Omada Identity manages user accounts and permissions for companies. The platform runs in the cloud to reduce security risks. It helps businesses follow compliance rules and manage user access.
Omada is widely recognized as one of the best IGA solutions for organizations seeking cloud-native identity governance.
Key Features:
- Cloud-Based System. Runs in the cloud without custom programming needs. Companies can set up the system fast. Scales automatically with business growth needs. Reduces infrastructure costs and maintenance work.
- Smart Compliance Tools. Checks if users follow company access rules automatically. Works with cloud and office systems at once. Automates compliance monitoring across all platforms.
- Complete User Monitoring. Shows what users do across all company systems. Tracks who accesses what data in real-time. Identifies unusual user behavior patterns quickly.
Pros:
- Does everything in one platform without extra tools reducing vendor management complexity
- Automates boring tasks so teams focus on important work improving productivity
- Pre-built compliance frameworks speed up regulatory compliance efforts significantly
- Cloud-native architecture provides better scalability than legacy solutions
Cons:
- Complex companies need lots of setup time initially requiring significant planning
- Works best in cloud but has fewer office options limiting hybrid deployments
- Limited vendor resources compared to established players
11. Ping Identity
Ping Identity protects company systems through its PingOne cloud platform. The system handles user login and security across different applications. It uses smart technology to spot security threats fast.
Key Features:
- PingOne Platform. One cloud system handles all user login needs together. Works with company applications both online and offices. Provides centralized control over all identity processes.
- DaVinci Work Engine. Automates user account tasks across cloud and office systems. Makes identity processes work together without manual steps. Creates custom workflows for specific business needs.
- Smart Security Engine. Uses AI to find suspicious user login patterns. Detects threats in real-time across all systems. Adapts security based on user behavior changes.
Pros:
- Connects different company systems so users log in once with single sign-on
- One platform handles all identity needs in one place reducing complexity
Cons:
- Full platform costs more than basic identity tools increasing budget requirements
- Better suited for managing your customers' logins rather than controlling what your own employees can access
- The advanced features are quite complex, so your IT team will need significant training to use it properly
How to Evaluate and Choose the Best IGA Solution?
You need to pick the right IGA solution for your business. Your company has special needs that change over time. The right pick saves you money and keeps hackers away.
Here are the things you should look for:
- User Access Management Features. You want one place to control who gets into what. Your IGA tool needs role-based access that works everywhere. Your people should only get the access they need.
- Policy and Compliance Management Tools. You need tools that make compliance reports by themselves. Your system should track every single thing users do. Audit reports should pop up without you doing anything.
- Automation Capabilities and AI-Powered Features. You should see how fast new users get set up. Your system needs to catch weird authentication methods right away. When people quit, their access should vanish instantly.
- Self-Service Features for Users. Your workers need to reset passwords without calling IT. People should ask for access through easy forms. Self-service cuts down your help desk work big time.
- Scalability and Performance Options. Your IGA solution must grow when your business grows. You need tools that work with thousands of people. Things should stay fast even when everyone logs in.
- Risk Management and Detection Capabilities. You want tools that watch for bad user behavior. Your system should warn you before hackers break in. Threat detection should happen every second of every day.
- Integration with Existing Systems. You should check if it connects to your current apps. Your SSO and MFA tools should plug in without coding. All your security stuff must work together perfectly.
- Analytics and Reporting Dashboard. You need reports that make themselves without your help. Your main screen should show what every user does. Compliance tracking should run by itself all the time.
- User Experience and Interface Design. You should pick systems that look simple and clean. Your people and IT team need screens that make sense. Learning how to use it should take almost no time.
- Security and Privacy Protection Features. You want IGA tools that lock up your data super tight. Your user info needs protection that hackers cannot break. Privacy rules should work by themselves across everything you use.
Strengthen Identity Governance with Infisign
Your IT team struggles with scattered permission management. Infisign creates centralized identity governance that works everywhere. Access policies enforce automatically across your entire infrastructure. Everything connects without replacing current tools.
The platform represents the best IGA solutions for large enterprises looking for quick deployment and modern security features.
- Automated User Lifecycle Management. New employees get correct access instantly. Departing staff lose access the moment they leave. No manual work delays or security gaps.
- Centralized Access Governance. Control all user permissions from one dashboard. Role-based access controls work across every system. No more scattered permission headaches.
- Real-Time Compliance Monitoring. Audit reports generate automatically for any regulation. Complete audit trails track every user action. GDPR and SOX compliance becomes effortless. Regulators get instant proof you follow rules.
- AI-Powered Access. Smart algorithms detect threats before damage happens. You get alerts about suspicious access patterns. Breaches get blocked automatically.
- Attribute-Driven Access Control. Create access rules once and enforce them everywhere. Policy-based access control (PBAC) and ABAC prevent conflicts automatically. Business rules become unbreakable security controls.
- Cross-Platform Integration. 6000+ API and SDK integrations work seamlessly together. Your current tools keep working perfectly.
Ready for Enterprise-Grade IGA Built for Speed, Scale, and Security? Get Started with Infisign Demo!
FAQs
What is the difference between IGA and IAM?
IGA manages who gets access to company systems. It watches user activities and tracks everything users do. This helps companies follow compliance rules and audit requirements. IAM controls the actual login process for users.
The key differences between IGA and IAM are:
- IGA Governance. It creates access policies and handles compliance reporting. IGA manages complete user lifecycle and access reviews.
- IAM Authentication. It verifies user identities during login. IAM manages passwords, multi-factor authentication, and real-time access control.
- Working Together. IGA creates rules, IAM enforces them. Both work together for complete identity security across organizations.
What are the core features of IGA Tool?
Iga software creates and removes user accounts automatically. Users request access through self-service portals easily. Role-based policies give people correct permissions for jobs. Risk detection finds dangerous access requests before damage happens. The system connects with existing company applications seamlessly. Leading vendors build complete solutions that work together perfectly.




























